导图社区 CISSP-7-安全运营
- 391
- 6
- 1
- 举报
CISSP-7-安全运营
CISSP-信息系统安全专业认证之安全运营思维导图,包括:基本概念、安全运营的基本概念、变更管理、配置管理、补丁和漏洞管理、事件管理。
编辑于2021-11-10 12:08:07- 相似推荐
- 大纲
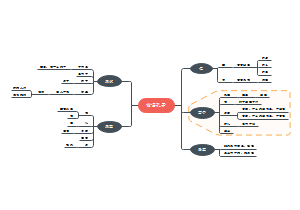
安全运营
基本概念
运行安全
在集中式和分布式环境中处理信息资产的保护和控制,
运行安全是其他服务的一个品质,并且它本身就是一组服务
安全运行
保持安全服务高效可靠的运行所要求的日常事务
业务连续性计划和灾难恢复计划
address the preparation, processes, and practices required to ensure the preservation of the organization in the face of major disruptions to normal organization operations are discussed. BCP and DRP involve the identification, selection, implementation, testing, and updating of processes and specific prudent actions necessary to protect critical organization processes from the effects of major system and network disruptions and to ensure the timely restoration of organization operationsif significant disruptions occur.
TOPICS
Investigations
Evidence collection handling
Reporting and documenting
Investigative techniques
Digital forensics
Investigation Types
Operational
Criminal
Civil
Regulatory
Electronic discovery (eDicsovery)
Logging and Monitoring
Intrusion detection and prevention
Intrusion detection and prevention
Continuous monitoring
Egress monitoring
Provisioning of Resources
Asset inventory
Configuration management
Physical assets
Virtual assets
Cloud assets
Applications
Foundational Security Operations Concepts
Need-to-know/least privilege
Separation of duties and responsibilities
Monitor special privileges
Job rotation
Information lifecycle
Service-level agreements
Resource Protection Techniques
Media management
Hardware and software asset management
Incident Response
Detection
Response
Mitigation
Reporting
Recovery
Remediation
Lessons learned
Preventative Measures
Firewalls
Intrusion detection and prevention systems
Whitelisting/Blacklisting
Third-party security services
Sandboxing
Honeypots/Honeynets
Anti-malware
Patch and Vulnerability Management
Change Management Processes
Recovery Strategies
Backup storage strategies (e.g., offsite storage, electronic vaulting, tape rotating) a Recovery site strategies
Multiple processing sites (e.g., operationally redundant systems)
System resilience, high availability, quality of service, and fault tolerance
Disaster Recovery Processes
Response
Personnel
Communications
Assessment
Restoration
Training and awareness
Disaster Recovery Plans
Read through
Walkthrough
Simulation
Parallel
Full interruption
Business Continuity Planning and Exercising
Physical Security
Perimeter
Internal
Personnel Safety
Objectives
■ Understand and support investigations.
■ Understand requirements for investigation types.
■ Conduct logging and monitoring activities.
■ Secure the provisioning of resources.
■ Understand and apply foundational security operations concepts.
■ Employ resource protection techniques.
■ Conduct incident response.
■ Operate and maintain preventative measures.
■ Implement and support patch and vulnerability management.
■ Participate in and understand change management processes (e.g., versioning,baselining, security impact analysis).
■ Implement recovery strategies.
■ Implement disaster recovery processes.
■ Test disaster recovery plan.
■ Participate in business continuity planning and exercising.
■ Implement and manage physical security.
■ Participate in personnel safety (e.g., duress, travel,
安全运营的基本概念
关键主题
维护运营弹性
When it comes to day-to-day operations, few things are more important than maintaining the expected levels of service availability and integrity. Organizations require critical services to be resilient. When negative events affect the organization, the operations staff is expected to ensure minimal disruption to the organization’s activities. This includes anticipating such disruptions and ensuring that key systems are deployed and maintained to help ensure continuity. They are also expected to maintain processes and procedures to help ensure timely detection and response.
关键业务有弹性 保持连续性
制订有应急预案
实时监控和响应
保护有价值的资产
Security operations are expected to provideday-to-day protection for a wide variety of resources, including human and material assets. They may not be responsible for setting strategy or designing appropriate security solutions. At a minimum, they will be expected to maintain the controls that have been put into place to protect sensitive or critical resources from compromise.
提供各种资产的日常维护
保护资产不被破坏
控制系统账号
Under the current regulatory environment, there has been a renewed focus on maintaining control over users (subjects) that have access to key business systems. In many cases, these subjects have extensive or unlimited capabilities on a given system; these are privileges that could be misused or abused. Operations security will be expected to provide checks and balances against privileged accounts as well as maintain processes that ensure that there continues to be a valid business need for them.
维护用户访问关键业务系统的控制
提供各种帐号(尤其是特权帐号)的检查和平衡,确保这些帐号成为合理的业务需求
有效管理安全服务
No security operations will be effective without strong service management and the processes that are put into place to ensure service consistency. These include key service management processes common to most IT services such as change, configuration, and problem management. It will also include security-specific procedures such as user provisioning and Help/Service Desk procedures. In today’s security operations, there is also considerable focus on reporting and continuous service improvement practices.
IT服务的变更、配置和问题管理
安全相关程序,如用户配资和服务台程序
关注报告和服务持续改进实践
运营人员的要求
prudent man负责、谨慎、明智和有能力的人
适度谨慎 due care
采取了合理的防范保护措施
适度勤勉 due deligence
在日常管理中尽到责任
控制特权账号
对帐号的数量和类型进行严格控制
using these solutions most effectively while also ensuring that privileged accounts are carefully
小心监控系统的帐号管理权限
服务帐号
执行脚本的帐号
Identity and access management (IAM)身份和访问管理
the provisioning of users用户配置
managing their access across multiple systems管理跨多系统的访问权限
native access control systems本地访问控制系统
知所必需和最小特权(互为补充)
need to know知所必需
基于工作或业务需要被授予最小知悉范围和访问权限
运营安全是关键
常用于军队s
Least privilege最小特权
要求用户或进程没有不必要的访问特权来执行工作、任务和功能
目标
限制用户和进程只访问必要的资源和工具来完成指定任务
限制
可访问的资源
用户可以执行的操作
使用组和角色管理账号
Efficient management of users requires the assignment of individual accounts into groups or roles. This will allow rights and privileges to be assigned to groups or a role as opposed to individual accounts When groups can be set up according to job functions within the organization, role-based access control (RBAC) can be used.
不同类型的帐号
特权帐号
Root or内置管理员帐号
用于管理设备和系统全能默认账号
安全控制
更名尽可能的严格
默认密码要修改
Logs记录个人使用 root账号的行为
使用root帐号远程登录时
会话应执行强加密和监控
使用多因子的身份验证方法
服务帐号
Systems use a variety of accounts to provide automated services, such as Web servers, email servers, and database management systems.
由系统服务和核心应用所使用的特权访问
密码复杂并经常更换
有一个策略来回收和关闭已遭泄露帐号
管理员帐号
These accounts are assigned only to named individuals that require administrative access to the system to perform maintenance activities, and they should be different and separate from a user's normal account.zhe
这些账号被分配给需要系统特权访问来执行维护任务的指定个人
这些账号应与用户的普通账号分开
账号密码应安全可靠的分发给个人
管理员应书面承认接收账号并遵守组织规则
账号不再使用应立即去除
所有的活动应该被审计
部署额外的日志系统
多因素认证
超级用户
这些账号权限由于工作所需授予超过普通用户权限但是不需要管理员权限的
超级用户可以在自己的桌面上安装软件
应书面承认接收账号并遵守组织规则,如签署安全协议书
普通或受限用户账号
使用用户最多
基于最小权限或知所必须原则
职责分离
定义:将一个关键任务分成不同的部分,每个部分由不同的人来执行
同谋
进行欺诈需要多人共谋
目的
制约,减少故意破坏的几率
补充,减少无意的疏漏和错误的几率
原因
不同安全相关任务所需技能不同
将管理员任务分成多个角色以赋予不同的信任级别
防止安全相关功能委托一个角色或人员
系统管理员
最小特权
根据需要确定必要访问和应用
监控
行为被日志审计并发送到一个 单独的审计系统中
防止欺诈行为
管理员如果没有勾结他人就没能力参与恶意活动
背景调查
岗位轮换
Job rotation ensures another individual must perform the original system administrator’s duties and also review their work.
操作员
System operators represent a class of users typically found in data center environments where mainframe systems are used.
工作职责
进行主机的日常操作,确保预定的工作有效进行和解决可能出现的问题
权限说明
操作员具有很高的权限,但低于系统管理员,这些权限可以规避系统的安全策略,应监控这些特权使用并进行日志审计
安全控制
最小特权
The systems operator often does not require access to every system and function in an organization. Determine what access is needed and apply accordingly.
监控
操作员的行动被记录并发送至不受操作员控制的一个独立系统中
职责分离
管理员如果没有勾结他人就没能力参与恶意活动An
背景调查
安全管理员
作用:定义系统安全设置并协同管理员进行相关配置,提供一种权利制衡,为系统管理员提供审计和审查活动
主要职责
账号管理
敏感标签的分配
系统安全设置
审计数据的评审
帮助/服务台人员
提供一线支持
在需要时重置用户密码
进行监控和背景调查
普通用户
需要访问信息技术资源
监控特权
许可、适用性和背景调查
以下情况不应被授予访问权限(如,基于IDS 和防火墙日志,应立即阻断某个IP的访问,但没有;调整时钟或删除日志等)
近期严重缺乏相关的判断力
有关角色的行为出现重复的高风险模式
角色的表现与非法活动有关.
Account Validation帐户验证
确定现有不活动账号(如,已离职/离岗人员帐户、临时休假人员帐户)
Job rotations岗位轮换
减少个人之间共谋活动的风险
双人操作
现场相互监督
强制休假
信息生命周期管理
Information has a life that consists of creation, use, and finally destruction信息生命周期包括产生、分发、使用、维护、披漏、处置(转让、安全处理)
information owner信息所有者
■ Determine the impact the information has on the mission of the organization.确定信息对组织使用具有的影响
■ Understand the replacement cost of the information (if it can be replaced)了解信息的重置成本(如果它可以被取代).
■ Determine who in the organization or outside of it has a need for the information and under what circumstances the information should be released.决定哪个组织需要这些信息和在什么情况下应该发布这些信息
■ Know when the information is inaccurate or no longer needed and should be destroyed.知道何时信息是不准确的或不再需要的,应当被销毁
Classification and categorization分级和分类
Classification is concerned primarily with access分级关注访问
■ Canada’s “Security of Information Act”12 ■ China’s Law on “Guarding State Secrets” 13 ■ The United Kingdom’s “Official Secrets Acts”14
military or government information.军队或政府信息(秘密、机密、绝密)
categorization is primarily concerned with impact分类关注影响.
N IS T ’s Special Publication 800-60 Volume 1 Revision 1 “Guide for Mapping Types ofInformation and Information Systems to Security Categories.”
determining the impact of the loss of confidentiality integrity, or availability of the information决定信息丧失机密性、完整性或可用性的影响(高、中、低,举例:对外发布的公共信息v.s.风险评估报告)
standardize the defense baselines可使基线标准化
保留计划
■ 降低存储成本
■ 只保存相关的信息,可加快搜索和索引
■诉讼保留和电子披露是不太可能会遇到错误,预决策或协商信息
(SLAs)服务水平协议
What
SLA是一个描述客户从供应商获得服务水平的简单文档,展示服务测量指标、补救或如果达不到协议要求所遭受的惩罚
如果由于客户的原因导致SLA达不到,则不应该受罚
SLA
外部
OLA(Operational Level Agreements
内部
Why
确保双方理解要求
确保协议没有被有意或无意的曲解
Who
不同的级别不同的价格
协商的起点
关键部分
Service elements
提供具体服务
服务可用性状态
服务标准(时间窗)
升级程序
各方职责
费用/服务权衡
Management elements
测量标准和方法定义\报告流程\内容和频率\争议解决过程
SLA保持更新
供应商能力和服务需求变化
赔偿
供应商将不得不向客户支付由于担保违规造成的任何第三方费用
SLA不能转让
如何验证SLA
statistics
测量指标
Service Availability
Defect Rates不良率
Technical Quality
Security
What Uptime Provisions Are Typical for Network Service Providers
99 percent availability (which allows for over 7 hours of unplanned downtime per month
99.9 percent (43.8 minutes per month)
99.99percent (4.4 minutes per month).
何时评审SLA
■ The clients business needs have changed (for example, establishing an e-commerce site increases availability requirements). ■ The technical environment has changed (for example, more reliable equipment makes a higher availability guarantee possible). ■ Workloads have changed. ■ Metrics, measurement tools, and processes have improved.
变更管理
变更管理流程
Requests 请求
Proposed changes should be formally presented to the committee in writing. The request should include a detailed justification in the form of a business case argument for the change, focusing on the benefits of implementation and costs of not implementing.
Impact Assessment影响评估
Members of the committee should determine the impacts to operations regarding the decision to implement or reject the change.
Approval/Disapproval 批准/不批准
Requests should be answered officially regarding their acceptance or rejection.
Build and Test构建和测试
Subsequent approvals are provided to operations support for test and integration development. The necessary software and hardware should be tested in a non-production environment. All configuration changes associated with a deployment must be fully tested and documented. The security team should be invited to perform a final review of the proposed change within the test environment to ensure that no vulnerabilities are introduced into the production system. Change requests involving the removal of a software or a system component require a similar approach. The item should be removed from the test environment and have a determination made regarding any negative impacts.
Notification通知
System users are notified of the proposed change and the schedule of deployment.
Implementation实施
The change is deployed incrementally, when possible, and monitored for issues during the process.
Validation验证
The change is validated by the operations staff to ensure that the intended machines received the deployment package. The security staff performs a security scan or review of the affected machines to ensure that new vulnerabilities are not introduced. Changes should be included in the problem tracking system until operations has ensured that no problems have been introduced.
Documentation记录
The outcome of the system change, to include system modifications and lessons learned, should be recorded in the appropriate records. This is the way that change management typically interfaces with configuration management.
配置管理
目标
建立和维护产品、系统和项目整个生命周期的完整性
the product, system, or item that is being managed throughout its lifecycle within the organization.
包括
identifying configuration items for the software project识别软件产品的配置项
controlling these configuration items and changes to them,控制配置项及其变更
recording and reporting status and change activity for these configuration items记录和报告配置项的状态和变更活动,同时开展审计
配置管理
discipline for evaluating, coordinating, approving or disapproving, and implementing changes in artifacts that are used to construct and maintain software systems
管理组件从最初的概念到设计、实施、测试、基线、构建、发布和维护
使得必然发生的变更可控
策略和标准
■ 组件集处于配置管理的支配下
■ 组件是如何命名的
■组建是如何输入和离开控制集的
■处于CM下的组件是如何被允许变更的.
■CM下的不同版本的组建是如何可用的
■在什么情况彼此每个都能使用
■CM工具是如何启动和加强配置管理的
The CMMI steps for CM
1.识别将要置于配置管理下的配置项、组件及其相关工作。
2.建立和维持配置管理和变更管理系统来控制工作产品
3.建立和发布内部使用基线以及交付给客户的基线.
4. 追踪配置项变更请求.
5. 控制配置项内容变更.
6. 建立和维持描述配置项的记录
7. 执行配置审计来维持配置项的完整性。
资产清单
硬件库
1. 品牌
2.型号
3. M A C addresses
4. 序列号
5. Operating system or固件版本
6. Location
7. BIOS and other hardware-related passwords
8. Assigned IP address if applicable
9.组织资产管理的标签或条形码
软件库
1. Software name
2. Software vendor (and reseller if appropriate)
3. 密码或激活码 (note if there are hardware keys)
4. Type of license and for what version
5. Number of licenses
6. License expiration
7. License portability
8. Organizational software librarian or asset manager
9. Organizational contact for installed software
10. Upgrade, full or limited license
软件库和硬件库的安全作用
安全专家能迅速找到和减少与硬件类型和版本相关的漏洞
知道网络中硬件类型和位置能降低识别受影响设备的工作量
可以经扫描发现网络中未经授权的设备
维护配置清单
记录和追踪配置的变更能提供网络完整性和可用性的保障
定期检查确保非授权变更
CM适用于不同类别资产管理
■ Physical assets (e.g., servers, laptops, tablets, smartphones)
■ Virtual assets (e.g., Software Defined Networks (SDNs), virtual SAN (vSAN)
systems, virtual machines (VMs))
■ Cloud assets (e.g., services, fabrics, storage networks, tenants)
■ Applications (e.g., workloads in private clouds, Web services, Software as a Service (SaaS))
security professional’s perspective
1 What are the requirements (legal, regulatory, business, governance, etc.) for the assets in question to be managed to?要求 2.Are there specific issues or concerns to be addressed based on the implementation or architecture of the assets? 3.Will there be more than one owner of the asset? If so, how many?所有者 4 .Who is/are the intended customer(s) for the asset?预期客户 5.When does the asset have to be available? (24x7, 9 to 5, Monday - Thursday, etc.)何时可用 6.How is the asset to be accessed and made available to the organization’s customers?如何访问 7. Where will the asset reside? On the LAN ? On the WAN in the Cloud? Will it be outsourced as a third party supported and provided solution? Will it be owned and maintained “in-house”?位置 8.Why is the asset being provisioned in the first place? What business need(s) is it designed to address?为什么进行业务配置,基于什么业务需求? 1.资产管理要求是什么? 2.具体问题是否基于资产的实施和架构处理的.
补丁和漏洞管理
补丁管理的目的
建立持续配置环境保护操作系统和应用的已知漏洞
The main objective of a patch management program is to create a consistently configured environment that is secure against known vulnerabilities in operating systems and application software.
很多时候厂商升级版本时不给出升级的原因和理由
■ http://cve.mitre.org - The Common Vulnerability and Exposures database that provides the standard naming and numbering convention for disclosed vulnerabilities ■ http://nvd.nist.gov - An online database of known vulnerabilities managed by the U.S. National Institute of Standards and Technology (NIST) ■ http://www.us-cert.gov - An online resource for a wide variety of information on known vulnerabilities and remediation options
补丁管理步骤
安全专家需要判断是否是漏洞
是否需要升级补丁
基于风险决策
What will be the risk if the flaw is not patched? Is the system likely to be exposed to threats that may exploit the vulnerability? Will special privileges be required for the vulnerability to be exploited? Can the vulnerability be used to gain administrative privileges on the target? How easy is it to exploit the vulnerability? W ill it require physical access to the system or can it be exploited remotely?
补丁的重要程度
管理层和系统属主来确定是否更新补丁
是否会影响到业务
更新补丁已经被测试以及残余风险被解决
安排更新
部署前通知用户
在夜间或周末更新
部属前备份服务器
更新完成后需要在生产环境中验证
可能会产生一些不可见问题
部署完成后确保所有适当的机器都被更新
记录所有变更
安全和补丁信息管理
关键部分
补丁管理是要知道关于安全问题和补丁发布两者的信息
知道与他们环境有关的安全问题和软件更新
建议专人和团队负责提醒管理员和用户的安全问题或应用的更新
Patch Prioritization and Scheduling 补丁优先级和作业安排
1、补丁生命周期(patch cycle) 指导补丁的正常应用和系统的更新
cycle
时间或事件驱动
帮助应用的标准补丁的发布和更新
2、作业计划处理关键安全和功能补丁和更新
patch priority and scheduling urgency
Vendor-reported criticality (e.g., high, medium, and low)
system criticality
importance of the applications and data the system
补丁测试
补丁测试的广度和深度
系统的关键度
处理的数据
环境的复杂度
可用性需求
可用资源
补丁测试流程开始于软件更新的获取和在生产部署后连续通过可接受性测试
补丁获取时需要进行验证
来源(soucre)校验
完整性(integrity)校验
数字签名
校验和
补丁校验完成后进行测试
测试环境尽可能的接近生产环境
可以用生产系统的子系统作为测试环境
补丁变更管理
变更对补丁管理的每一步都非常重要
修补应用程序应包含应急和回退计划
在变更管理方案中包含风险降低策略
变更管理方案中包含监控和可接受计划
证明补丁成功具体里程碑和可接受标准
允许关闭变更系统中更新
补丁安装和部署
补丁管理的部署阶段必须具有良好经验的管理员和工程师
安装和部署意味着生产系统的补丁和更新会真实实施
影响补丁部署的技术因素是工具的选择
工具选择
购买
自建
工具类型
agent-based
agentless systems,
部署安全补丁
及时完成
可控和可预期
补丁审计和评估
常规审计和评估能衡量补丁管理成功和程度
两个问题
对于任何已知漏洞或Bug什么系统需要修补?
系统是否更新真实的补丁?
关键成功因素
资产和主机管理
理想主机管理软件能声称报告
管理工具
Tivoli, UnicenterTG, or System Center Configuration Manager
系统发现和审计作为审计和评估流程的部分
System discovery tools
uncover these systems and assist in bringing them under the umbrella of formal system management and patch compliance.
一致性和复合型
补丁管理方案中的审计和评估元素能帮助识别系统不符合组织指南或其他减少不符合的工作
System build tools and guidelines are the primary enforcement means of ensuring compliance with patch requirements at installation time. 系统声称工具和指南在安装时确保符合补丁要求主要执行手段
补丁管理技术非常重要,但仅靠技术不行
补丁管理方案是团队技术提供基于协作解决组织独特要求的方针和运维的解决方案
漏洞管理系统
Sun Tzu once wrote, “If you know the enemy and know thyself, then you need not fear the result of a hundred battles.” The two principal factors needed for an organization to “know thyself” involve configuration management and vulnerability scanning.
配置管理
帮助组织知道其所有部分
脆弱性扫描
Vulnerabilities arise from flaws, misconfigurations (also known as weaknesses), and policy failures.
识别这些弱点
漏洞类型
系统缺陷
product design imperfections
buffer overflow
配置错误
represent implementation errors that expose a system to attack.
策略错误
individuals fail to follow or implement security as required
基于主机的扫描
conducted at the system console or through the use of agents on servers and workstations throughout the
identifying missing security updates on servers
identify unauthorized software or services that might indicate a compromised system
应用安全扫描
数据库安全扫描
发现配置错误
事件管理
Security professionals manage the day-to-day operations of key security services as well as participate in cross-enterprise processes. The security professional must understand the many types of security technologies that are deployed. The security professional should also understand the role that security plays in operational processes such as change, configuration, incidet, and problem management.
事件管理
包含人、技术和流程
指导所有与事件有关的活动并指导安全人员到一个预定义和预授权路径的解决方案。
描述在事件中所包含的各方的角色和职责中所采取的活动。
管理安全技术
There is a large number of technical controls deployed at most enterprises. These controls need to be maintained and managed effectively if they are to be trusted to protect the enterprise. They will also be necessary to quickly alert the security professional when security incidents occur and assist them to respond more effectively. In security operations, the focus is less on the technologies themselves and more on the ways that they are managed in an operational environment.
边界控制
更可信和不可信环境之间的划分
firewalls, routers, proxies, and other technologies
单个系统
在核心功能和终端用户流程
安全运营关注确保技术能够有效运行,并持续监控其有效性
安全测量指标和报告
测量安全控制的有效性
安全技术
ID/IPS
attacks that were detected or blocked and检测或阻断攻击
provide trending over time提供趋势分析
防火墙
common sources of attacks through IP addresses and other means通过IP地址追踪攻击源和其他方式
Email security services安全邮件服务
on the amount of malware or spam that is being detected and blocked发现或阻断大量的恶意软件或垃圾邮件
关注指标(病毒爆发台次、攻击源IPtop10、垃圾邮件发现或清除数量及比例)
报告
fundamental to successful security operations报告是安全运营的基础
报告的预期受众
技术报告趋向于为技术专家或直接服务交付的经理设计
Management reporting管理报告
provide summaries of multiple systems as well as key metrics for each of the services covered by the report提供多系统的综述以及报告所覆盖的每个服务的关键指标
Executive dashboards高管仪表板
in seeing only the highlights across multiple services跨多个服务的突出显示部分
provide simple summaries of the current state,为高管提供当前状态的综述
usually in a highly visual form like charts and graph以图表等高度可视的形式展现
报告频率
operational level
yearly, monthly, weekly, or even daily,
监测
入侵检测预防与系统
identify and respond to suspected security-related events in real time or near real time.用来识别和应对实时或近实时的可疑安全相关事件
Network-based intrusion systems
focus on the analysis of network traffic基于网络流量分析
host-based intrusion systems
focus on audit logs and processes inside a single system基于单个系统的审计日志和流程
IDS
out-of-band
IPS
in-line
Signature- or Pattern-Matching systems模式匹配(或签名分析)
Examine the available information (logs or network traffic) to determine if it matches a known attack.
Protocol Anomaly-Based systems基于异常协议的入侵检测系统
Examine network traffic to determine if what it sees conforms to the defined standard for that protocol, for example, as it is defined in a Request for Comment or RFC.基于已知的网络,检测其是否符合协议标准.
Statistical-Anomaly-Based systems基于统计异常的入侵检测系统
Establish a baseline of normal traffic patterns over time and detect any deviations from that baseline. 建立行为 Some also use heuristics to evaluate the intended behavior of network traffic to determine if it intended to be malicious or not. Most modern systems combine two or more of these techniques together to provide a more accurate analysis before it decides whether it sees an attack or not.
False-positives
误报
False-negatives
漏报
防恶意软件系统
installed on individual hosts, on systems部署在单个主机和系统上
Unified Threat Management(UTM)安全网关
continual updates持续更新病毒库
monitored to ensure they are still active and effective通过监控来确保防病毒系统始终存活和有效
automatic scanning for new media and email attachments.部署介质和邮件附件自动扫描策略
Scanning should be scheduled and accomplished on a regular basis.扫描应给定期安排和实施
(SEIM)安全信息事件管理系统
One disadvantage of system logs is that they provide a view into that single system系统日志的缺点是只能提供单个系统的视角,不能提供相关事件的涉及多个系统的日志和信息
provide a common platform for log collection, collation, and analysis in real time提供一个公共平台,用于日志收集、整理、实时分析。
provide reports on historical events using log information from multiple sources提供使用来自多信息源并关于历史事件的报告
Log management systems are similar日志管理系统是类似的
combined with S E IM solutions结合SEIM解决方案
real time functions提供实时分析.
maintain a disciplined practice of log storage and archiving维护严格的日志存储和归档纪律
Modern reporting tools can also be used to transform security event information into useful business intelligence.当今的报告工具可以将安全事件信息转换为有用的业务智能
响应
When an incident is detected, a containment strategy must be decided disconnecting devices from the network, shutting systems down, or redirecting traffic around an affected area of the network The team should instead focus on obtaining a forensic image of the RAM and hard drive of the compromised system and then determine how to mitigate the vulnerability that caused the compromise.
遏制策略 (举例:从网络中切断病毒源、控制受感染的主机)
■ The need to preserve forensic evidence for possible legal action.以合法行为来保存法庭证据
■ The availability of services the affected component provides.提供受影响的组件,保持服务的可用性
■ The potential damage that leaving the affected component in place may cause.替代受影响组件,避免可能造成的潜在损害
■ The time required for the containment strategy to be effective.需要时间来实施有效的遏制策略
■ The resources required to contain the affected component.需要资源来遏制受影响的组件
延迟遏制策略导致更深的影响
lead to further attack
起始事件以及相关信息应尽可能多的被记录
越来越多的信息应该汇聚在一起,直到该事件被安全运营团队认为是解决了
报告
Some organizations are required to report incidents that meet certain conditions
Policies and procedures政策和程序必须定义
defined to determine how an incident is routed when criminal activity suspected.
■ Does the media or an organizations external affairs group need to be involved?媒体或组织的外部事务组需要参与吗?
■ Does the organizations legal team need to be involved in the review?组织的法律团队需要参与评审吗?
■ At what point does notification of the incident rise to the line management,该事件在什么时间点应该上升到一线管理人,并通知中层管理人。
middle management, senior management, the board of directors, or the stakeholders?高层管理人?董事?股东的董事会?
■ What confidentiality requirements are necessary to protect the incident information?保护事件信息的保密性要求是什么?
■ What methods are used for the reporting? If email is attacked, how does thatimpact the reporting and notification process?用于报告的方法是什么?如果电子邮件系统被攻击,那么如何启动报告和通知程序?手机、固化,应急联系人?
恢复
恢复计算机映像到无损失
恢复的第一步是根除
Eradication is the process of removing the threat根除是消除威胁的过程。(如果一个系统感染了病毒而无法正常工作,那么彻底杀毒将根除这一问题。)
将系统恢复或修复到一个已知的良好状态。
如果最后已知的映像或状态包含有实际造成事件的原因, 那么恢复变得非常复杂,这种情况下,新得映像应该生成, 并在应用移入生产环境前测试.
修复和审查(经验教训)
事件响应最重要的是总结经验教训
(RCA)根本原因分析
reviewing system logs, policies, procedures, security documentation, and network traffic capture if available to first piece together the history of the event that caused the incident
work backwards to determine what allowed the event to happen in the first place.逆向工作来决定事件发生的原因,层层向前推演,直到发现根源
R CA can quickly cross boundaries between technical, cultural, and organizational.RCA可迅速跨越技术、文化和组织之间的边界界限。
Remediation修复
from R C A are then reviewed by management for adoption and implementation根源分析被管理层评审,决定是否采纳和执行
问题管理
Incident and problem management are intimately related
incident management
managing an adverse event管理不良事件
limiting the effect of an incident,限制一个事件的影响。
problem management
tracking that event back to a root cause and addressing the underlying problem跟踪该事件回到事件根源和解决的根本问题
addressing defects that made the incident possible or more successful.关于解决缺陷,使得该事件可能成功或更成功。
have a longer term view需要更长的时间
incidents as they occur in the operational environment在操作环境中发生的事件的长期过程
track down the underlying defect because it may take specific conditions to be in place that may not occur frequently可能需要特定的条件,这个条件可能不回频繁发生。
安全审计和评审-缓解前兆
安全审计
performed by an independent third party由独立第三方实施
determines the degree with which the required controls are implemented.确定实施控制所需程度
Internal reviews内部评审
conducted by a member of the organization's staff that does not have management responsibility for the system.由不负责该系统管理的组织成员来实施
External reviews外部评审
involve outside entities that evaluate the system based on the organizational security requirements.基于组织安全需求由外部实体来评价系统
provide an independent assessment of the system提供系统的独立评审.
security review安全评审
conducted by the system maintenance or security personnel to discover conducted by the system maintenance or security personnel to discover由系统维护或安全人员实施,来发现系统的漏洞
vulnerability assessment脆弱性评估
Penetration testing渗透测试
be conducted with physical access to the system or from the outside of the system and facility.
The outcome of the security audit and review process安全审计和评审的输出应列为将要有组织解决的项目和问题
should be a list of items and issues that have to be addressed by the security actors in the organization.
调查
名词解释
数字调查
One area that has traditionally been lacking in most organizations is proper evidence handling and management.
computer forensics, digital forensics, and network forensics to electronic data discovery, cyber forensics, and forensic computing.
基于有方法的、可验证的和可审计的程序和协议
American Academy of Forensic Sciences (AAFS)美国法庭科学技术学会
Digital Forensic Science Research Workshop (DFRWS)数字法医学研究研讨会
为促进和加强发现犯罪事件的重建或者帮助预判非授权活动会终端计划运行,使用科学导向和证实的方法提取来自数据源的数字证据进行保护、收集、验证、识别、分析、解释、记录和展示。 “The use o f scientifically derived and proven methods toward the presentation, collection, validation, identification, analysis, interpretation, documentation and presentation o f digital evidence derived from digital sources for the purpose o f facilitating or furthering the reconstruction o f events found to be criminal, or helping to anticipate unauthorized actions shown to he disruptive to planned operations As 'a forensic discipline, this area deals with evidence and the legal system and is really the marriage o f computer science, information technology, and engineering with law. The inclusion o f the law introduces concepts that may be foreign to many security practitioners and security professionals. These include crime scene, chain o f custody, best evidence, admissibility requirements, rules o f evidence, etc. It is extremely important that anyone who may potentially be involved in an investigation is familiar with the basics o f dealing with and managing evidence. There is nothing worse than finding the proverbial smoking gun only to learn that the evidence cannot be used, will be suppressed, or, even worse, the information security professional has violated the rights o f the individuals in question and is now in worse trouble than the “bad guys.” Although different countries and legal systems have slight variations in determining how evidence and the digital crime scene should be handled, there are enough commonalities that a general discussion is possible.1
取证指南
Identifying Evidence 识别证据
正确识别犯罪场景、证据和潜在的证据容器; Correctly identifying the crime scene, evidence, and potential containers of evidence.
Collecting or Acquiring Evidence搜集或获取证据
秉承刑事罪证查验原则以及确保场景的污染和破坏保持最小,使用可靠和可重复的收集技术来展示证据或证据拷贝的精确性和完整性Adhering to the criminalistic principles and ensuring that the contamination and the destruction of the scene are kept to a minimum. Using sound, repeatable, collection techniques that allow for the demonstration of the accuracy and integrity of evidence or copies of evidence
Examining or Analyzing the Evidence检查或分析证据
使用可靠的科学方法来确定证据的特征,进行个别证据对比以及事件重构Using sound scientific methods to determine the characteristics of the evidence, conducting comparison for individuation of evidence, and conducting event reconstruction
Presentation of Findings展示证据
解释来自于基于事实的发现的检查和分析的输出以及以一种适合特定观众的格式进行阐述Interpreting the output from the examination and analysis based on findings of fact and articulating these in a format appropriate for the intended audience (e.g., court brief, executive memo, report).
犯罪场景
Before the security professional can begin to identify evidence, the larger crime scene needs to be dealt with. A crime scene is nothing more than the environment in which potential evidence may exist. The same holds for a digital crime scene.
形式原则
1. Identify the scene确定现场,
2. Protect the environment保护环境,
3. Identify evidence and potential sources of evidence确定证据和证据的潜在来源,
4. Collect evidence收集证据,
5. Minimize the degree of contamination降低污染度
环境
物理环境
server, workstation, laptop, smartphone, digital music device, tablet
处理相对简单 relatively straightforward to deal with;
虚拟环境
很难确定证据真正的位置或获取证据 difficult to determine the exact location of the evidence or acquire the evidence,
e.g., data on a cluster or GRID, or storage area networks (SANs))
动态证据
数据存在于动态的运行环境中
more difficult for the security professional to protect the virtual scene
动机 ,机会,和方式 MOM
动机
谁,为什么
机会
何时,何地
方式
罪犯需要获得成功的能力
计算机犯罪行为
惯用手法MO
罪犯使用不同的操作手法进行犯罪,这可以用于帮助标识各类犯罪
罗卡交换定律
认定罪犯在带走一些东西的时候会遗留下一些东西
General Guidelines G8
(e.g., United States National Institute of Standards and Technology (NIST), United States Department of Justice (DOJ)/ Federal Bureau of Investigations (FBI) Search and Seizure Manual, NIST SP 800-86: Computer Forensic Guidelines, SWGDE Best Practices for Computer Forensics, ACPO Good Practices Guide for Computer Based Evidence, IACIS forensic examination procedures).
当处理数字证据是,必须应用所有通用取证和程序原则.
抓取证据的行为不能改变证据.
当人员有必要访问原始数字证据时,这个人需要以此为目的进行培训.
所有与数字证据的扣押、访问、存储或传输有关的活动必须被完全记录、保留并在评审检查时可用.
当数字证据在某人身上时某人必须为所有关于数字证据的活动负责.
任何负责抓取、访问、存储和传输数字证据的机构对符合这些原则负责。
rules of thumb
■ Minimize handling/corruption of original data.
■ Account for any changes and keep detailed logs of your actions.
■ Comply with the five rules of evidence.
■ Do not exceed your knowledge.
■ Follow your local security policy and obtain written permission.
■ Capture as accurate an image of the system as possible.
■ Be prepared to testify.
■ Ensure your actions are repeatable.
■ Work fast.
■ Proceed from volatile to persistent evidence.
■ Do not run any programs on the affected system.
事件处理的 策略、角色和职责
To have effective and efficient incident handling, an organization must possess a solid foundation of knowledge and policy 事件响应和处理策略、顾虑各种应对事件法律问题的清晰明确的程序和指南、证据的处理和管理
策略必须清晰、简明、并对事件响应/处理团队授权来处理任意和所有的事件
配备人员并经过良好培训的事件响应团队
虚拟团队
专职团队
混合模式团队
外包资源
A fourth model that some organizations are using would involve outsourced resources that are available “on-demand” for participation in an investigation or as members of a response team.
响应团队的核心领域
legal department (in lieu of inhouse legal counsel, arrangements should be made with external counsel), human resources, communications, executive management, physical/corporate security, internal audit, IS security, and IT. 法律部门(内外部的法律顾问都可以)、人力资源、通信、高管、物理/企业安全、内部审计、IS安全以及IT部门等,也包括先关业务部门、系统管理员和任何能够辅助进行事件的调查和恢复的人员
团队建立好需要进行培训并保持最新的培训,需要耗费极大的资源
Once the team has been established, it must be trained and stay current with its training.
小心处理公共消息披露
事件响应
事件响应或事件处理已经成为组织安全部门的主要职责
Computer Emergency Response Team Coordination Center (CERT/CC), AusCERT Forum of Incident Response Teams (FIRST), NIST British Computing Society Canadian Communications Security Establishment (CSE)),
通用框架
建立事件响应能力Creation of a response capability;
事件处理和响应Incident handling and response;
恢复和回馈Recovery and feedback;
事故处理和响应
If the appropriate groundwork has been laid, the next phase is the actual handling of an incident. triage, investigation, containment, and analysis and tracking.
定义
事件是一个可被观察、验证和记录在案的消极事情
事故是给公司及其安全状况造成负面影响的一系列事件
事故响应:某些事情给公司造成影响并引发了安全违规,诸如此类应对问题成为事故响应或事故处理
步骤
诊断
包含事件的检测、识别和通知等子阶段;
根据事件潜在风险级别进行归类,这受到事件类型、来源(内部事件还是外部事件)、增长速度、错误抑制能力的影响;
处理假阳性事件( false-positive )/误报时最耗时间的;
如果是真实事件,则需要进行分类(基于组织的需求)和分级(确定潜在风险的等级或事件的关键度)
调查
the desired outcomes of this phase are to reduce the impact of the incident, identify the root cause, get back up and running in the shortest possible time, and prevent the incident from occurring again
直接处理事件的分析、解释、反应和恢复;
调查涉及对相关数据的适当收集,收集的数据将在分析和随后的阶段中使用;
管理层必须确定执法部门是否参与调查,是否为起诉而收集证据,或者是否只修补漏洞;
遏制
遏制事件,降低事件的影响;
遏制措施应当基于攻击的类别、受事故影响的资产以及这些资产的关键程度;
适当的遏制措施为事故响应团队争取了对事件根本原因进行正确调查和判定的时间;
必须维持适当的记录以及证据潜在来源的处理;
分析和追踪
在分析阶段收集更多的数据(日志、视频、系统活动等),从而试图了解事件发生的根本原因,并确定事件的源头是内部还是外部,以及入侵者如何渗透的;
安全专家需要结合正式的培训以及真实经验来作出适当的解释,往往没有足够的时间;
追踪往往与分析和检查并行,而且需要剔除错误线索或故意的欺骗的源;
另外比较重要的是一旦根源被识别以及追踪到真正的源头时需要做什么。
Objective
obtain sufficient information to stop the current incident
prevent future “like” incidents from occurring
identify what or whom is responsible
恢复阶段
目的是使得业务得以恢复和运行、让受影响的系统恢复生产,并与其他活动一致;
进行必要的修复工作,以确保此类事件不会再次发生;
修复工作包括:阻止敏感端口、禁用易受攻击的服务或功能、打补丁等。
报告和记录
最重要也最容易忽视的阶段就是汇报和反馈阶段;
组织往往能在事件中学习甚多,并从错误走向成功;
汇报需要所有的团队成员,包含受事件影响的各个团队的代表;
优点就是该阶段能从收集有意义数据中开发或追踪响应团队的绩效;
测量指标可以决定预算配置、人员需求、基线、展示审慎和合理性;
难点在于产生对组织有意义的统计分析和指标。
证据收集和处理
证据保管链
其所指的是证据介质从最初的采集、标识,到运输、使用、中间的保管及最后的存放和归档,都要有明确记录(Document)、职责归属(Accountability),以确保原本的证据介质完全没有任何机会被污染(Contaminate)和篡改(Tamper);
在整个证据的生命周期过程中,都是关于证据的处理的who, what, when, where, and how;
确保证据的真实性和完整性( authenticity and integrity),借助Hash(SHA-256)和数字签名;
访谈
调查过程中最为微妙的部分,就是证人和嫌疑人的访谈;
访谈前必须要审视策略、通知管理层以及联系公司法律顾问;
访谈过程不要单独一人,如果可能,录下整个访谈过程作为佐证;
理解取证程序
可被法庭接受的证据
证据分类
呈现方式分类
书面的
口头的
证人所作证词
计算机生成的
视觉的或听觉的
犯罪过程中或犯罪刚结束时所捕获的事件
按影响力分类
最佳证据
原始合同
辅助证据
口头证据、原始文件的复印件
直接证据
证人的证词
基于证人五种感官收集的证据
决定性证据
间接证据
证实中间事实,中间事实可用于推论或认定另一事实的存在
确定性证据
支持行证据,用来帮助提供一个想法或观点
观点证据
专家证人提出的教育观点
一般证人只能对事实作证
传闻证据
法庭上陈述的口头或书面证据,是二手的
证据特征
真实性或相关性
必须与调查结果有着适度的和切合实际的关系
完整性
证据必须呈现全部真相
充分性或可信性
必须有充分的说服力来使一个讲道理的人相信调查的真实性,证据必须有力,不容易被怀疑
可靠性或准确性
必须与事实一致。如果他是基于一个人的观点或是原始文件的复印件,那么证据就不是可靠的
计算机日志
前提是他们必须是在业务的规范过程中收集的,业务记录特例
大多数与计算机相关的文件别认为是传闻,即第二手证据
取证原则
调查的任何行动不得改变存储介质或数字装置中的数据;
访问数据的人员必须有资格这么做并有能力解释他们的行为
适用于第三方审计并应用于流程的审计痕迹或其他记录应被生成和保护,并精确的记录每个调查步骤
负责调查的人必须完全对确保以上提到的层序负责并遵守政府法律
关于人员抓取数据的行为不得改变证据
当有必要人员访问原始证据时,这个必须具有法律资格
与数字证据的抓取、访问、存储或传输有关的行为必须小心的记录、保存并可用于审计
当数字证据为某人持有时,这个人必须为证据所采取的行动完全负责
澳大利亚计算机取证通用指导原则
对原始数据的处理或讹误保持最小化
记录所有动作并解释变化
遵循证据的5个原则(可接受、可靠、完整、准确、有说服力)
处理和/或扽系证据超出自己的知识、技能和能力时,寻求更有经验的人的帮助
遵循组织结构的安全策略,并获得管理支配取证调查的书面许可
尽可能快速、准确得捕获系统的一个镜像
为在法庭上作证准备
区分你的动作优先顺序,从易失证据直至永久证据
不要再可能成为证据的系统上运行任何程序
在管理取证调查时具备道德和诚意,并且不试图进行任何破化
证据分析方式
介质分析:从信息介质中恢复信息或证据;
网络分析:从使用的网络日志和网络活动中分析和检查作为潜在的证据;
软件分析:分析和检查程序代码(包括源代码、编译代码和机器码)、利用解码和逆向工程技术、包括作者鉴定和内容分析等;
硬件/嵌入式设备分析:应包含移动设备的分析;
■ No actions performed by investigators should change data contained on digital devices or storage media. ■ Individuals accessing original data must be competent to do so and have the ability to explain their actions. ■ An audit trail or other record of applied processes, suitable for independent third-party review, must be created and preserved, accurately documenting each investigative step. ■ The person in charge of the investigation has overall responsibility for ensuring the above mentioned procedures are followed and incompliance with governing laws. ■ Upon someone seizing digital evidence, actions taken should not change that evidence. ■ When it is necessary for a person to access original digital evidence, that person must be forensically competent. ■ All activity relating to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review. ■ An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in his or her possession.
调查类型需求
需求
These problems are compounded by the relative anonymity afforded by the Internet as well as the transcendence of geographical and physical limitations in cyberspace, both of which render difficult the detection of criminals who are able to take advantage of a virtually limitless pool of victims.
an expression of desired behavior.
deals with objects or entities,
the states they can be in,
the functions that are performed to change states or object characteristics.
计算机犯罪
any illegal act fostered or facilitated by a computer, whether the computer is an object of a crime, an instrument used to commit a crime, or a repository of evidence related to a crime
计算机促进和协助的非法行为,不管计算机是犯罪目标、犯罪工具还是与犯罪有关的证据存储。
第一响应人
In sum, to preclude vulnerabilities in the prosecutor’s case and to adequately defend against any related challenges, care must be exercised by first responders during the search and seizure of computer equipment
critical import
犯罪调查三要素
Information accumulation信息累积:是调查的基本要素
Instrumentation工具:工具在调查财务相关犯罪时涉及计算机系统主要围绕追踪和分析确定在正常模式下的差异或违规的日志和记录;
Interviewing访谈:为调查者提供间接工具,如深入动机和可能所使用的技术,尤其是攻击者是内部人员时;
持续和出口监控
Continuous Monitoring as a Service (CMaaS)持续监控及服务,由美国政府所驱动,关注网络防御并内置于基础设施中提供所需服务
Egress Monitoring 出口监测
Egress filtering is the practice of monitoring and potentially restricting the flow of information outbound from one network to another.
出口过滤机制是监控的实践以及潜在限制从网络的一遍到另一边的信息流;
从私有网络到互联网的信息流应被监控和控制;
应严格的控制、监视和审计网络流量;
使用物理和逻辑访问控制机制影响和管理网络流量和带宽;
每当新应用需要外部网络访问可能需要策略的变更和行政管理机制;
边界装置检查离开内网的数据包并验证所有出站数据包源IP地址属于分配的内部地址块,防止内网收到IP地址的Spoofing(欺骗)攻击;
设计的持续监控系统符合机构需求;
实施持续监控系统并保护机构关键设施;
具体可关注“第六章 安全评估和测试”中“收集安全数据”部分
几种计算机犯罪
salami攻击
供给者实施几个小型的犯罪,希望他们结合起来的较大犯罪不会引起人们的注意
数据欺骗
对现有数据的更改
密码嗅探
捕捉计算机之间发送的密码
IP欺骗
攻击者不想让其他人知道自己的真实地址,从而改变数据包IP地址,使其指向另一个地址。
垃圾搜索
翻看其他人的垃圾箱,以寻找丢弃的文件、信息和其他可用来对该人或公司不利的珍贵物品。
搭线窃听
一种被动攻击,用于窃听通信的工具可以是无线电话扫描器、无线电接收器、麦克风接收器、录音器、网络嗅探器等。
域名抢注
是指有人怀着用一个类似域名损害公司或者进行敲诈勒索的目标,购买了一个域名。
资源保护
保护企业有价值的资产而不是全部资产
有形和无形资产
Tangible assets are physical and fall under the category of traditional property.
Intangible assets are not physical and fall under the categories of intellectual property.(专利证书、特许经营权)
设施防护
设施需要适当的系统和控制来维持它的运营环境
Fire detection and suppression systems
Heating, ventilation, and air conditioning systems
Water and sewage systems are an integral part of any facility
power supply and distribution system
Stable communications
facility access control and intrusion detection system
硬件
硬件需要适当的物理安全措施来维护所需要的机密性、完整性和可用性
操作员终端和工作中应限制访问
应限制设施的访问
应保护移动资产
打印设施应位于授权用户附件
网络装置属于核心资产应需要保护
介质管理
类型
Soft-copy media
magnetic, optical, and solid state
flash drives and memory cards.
hard-copy media
paper and microfiche.
介质保护
Media containing sensitive or confidential information should be encrypted
data should be protected through the use of encryption to mitigate a compromise.
特殊类型的介质
product software
Original copies and installed versions of system and application
controlled through a software librarian.
移动介质
问题
组织不知道信息何时离开
组织不知道信息是否被泄露
用户一般不会报告违规.
解决建议
组织实施DLP
a Monitoring and restriction of USB and other external ports
a Monitoring of DVD, Blu-ray蓝光, and other writable disk drives
安全移动介质管理方案
强制加密使用强认证
监控和记录传输到介质的信息
库存保管能力
远程擦除能力
定位地理位置的能力
归档和离线存储
Backups and archives are two different types of methods used to store information
backup
基于常规基础并在灾难发生时用于恢复信息或者系统
包含用户日常处理的信息
archive.
信息由于历史目的,且没有持续使用,应保存并从系统中移除
Recovery from backups
have well-defined and documented procedures to ensure that restorations are done in the right order.
all backup and archival media is tested regularly
云存储和虚拟存储
Cloud storage
digital data is stored in logical pools
may be accessed through a co-located cloud compute service, a Web service application programming interface (API), or by applications that utilize the API,
Cloud storage services
■ Made up of many distributed resources, but it still acts as one.
■ Highly fault tolerant through redundancy and distribution of data.
■ Highly durable through the creation of versioned copies.
several concerns
When data is distributed, it is stored at more locations, increasing the risk of unauthorized physical access to the data.
The number of people with access to the data who could be compromised (i.e., bribed or coerced) increases dramatically.
It increases the number of networks over which the data travels
When you are sharing storage and networks with many other users/customers, it is possible for other customers to access your data, sometimes because of erroneous actions, faulty equipment, a bug, or because of criminal intent.
Virtual storage
定义
指将多个不同类型、独立存在的物理存储体, 通过软、硬件技术,集成转化为一个逻辑上的虚拟的存储单元, 集中管理供用户统一使用。
benefit
that commodity hardware or less expensive storage can be used to provide enterprise-class functionality.
primary types of virtualization
Block virtualization
Block virtualization refers to the abstraction (separation) of logical storage (partition) from physical storage so that it may be accessed without regard to physical storage or heterogeneous structure. 数据块虚拟化是指抽象 (分离) 的逻辑存储 (分区) 从物理存储以便它可以访问物理存储或非均质结构。
abstraction (separation) of logical storage
File virtualization
File virtualization eliminates the dependencies between the data accessed at the file level and the location where the files are physically stored. 文件虚拟化消除了在文件级安数据访问和物理上存储文件的位置之间的依赖关系。
Types
Host-based
Host-based virtualization requires additional software running on the host, as a privileged task or process. volume management(磁卷管理) is built into the operating system, and in other instances it is offered as a separate product.
Storage Device-based
A primary storage controller provides the virtualization services and allows the direct attachment of other storage controllers.
The primary controller will provide the pooling and metadata management services
Network-based
storage virtualization operating on a network-based device (typically a standard server or smart switch) and using iSCSI or Fibre Channel (FC) networks to connect as a SAN.
most commonly available and implemented form
硬拷贝记录
记录和信息管理程序 (RIM)
are essential activities to protect business information and can be established in compliance with laws, regulations, or corporate governance.
确保信息在组织遭遇灾难时可用
保护硬拷贝记录
Additional resources for the security professional to use are: ■ ANSI/ARMA 5-2010, Vital Records Programs: Identifying, Managing, and Recovering Business-Critical Records sets the requirements for establishing a vital records program; ISBN: 978-1-931786-87-4 ■ A R M A Guideline for Evaluating Offsite Records Storage Facilities (PDF); ISBN: 978-1-931786-31-7
风险
Loss of or damage to paper records can occur from fires, floods, hurricanes
处置建议
Strategies for protecting vital hard-copy
documents include storing them in secure, clean, and environmentally stable containers;
making backup copies and storing the backups in secure off-site areas with stabilized temperature and humidity;
making microfiche copies制作微缩胶卷拷贝
处置和重用
应小心清除残留数据
简单删除或格式化
simply remove the pointers to the information.
软件清除工具
使用随机或预定的模式覆写磁介质的每一个部分
缺点
一次性覆写易被恢复,对于敏感信息应多次覆写
易被实验室工具恢复
剩磁
衡量介质中残存的磁场,以某种方式擦除信息剩余部分的物理表现
不安全
消磁
使用电磁场消除磁性
就是降低介质上的磁场到零.
比较安全的处理方法
物理销毁
粉碎、燃烧、研磨是常见的方法
最安全,但要注意颗粒度
资源保护技术
Operations can be impacted by a variety of threats. These threats may be caused by individuals or environmental factors. A security practitioner who is aware of common threats will be more prepared to propose or implement controls to mitigate or limit the potential damage
Unauthorized Disclosure非授权泄密
是一种值得关注的威胁
恶意软件的恶意活动以及恶意用户都会导致重要信息的丢失
破坏、中断和盗窃
Malicious activity on the part of malware and malicious users can cause the loss of a significant amount of information.
Interruptions in service can also be extremely disruptive to normal business operations
Failure of equipment, services, and operational procedures can cause system components to become unavailable. Denial-of-Service (DoS) attacks and malicious code can also interrupt operations.
Theft is also a common threat.
腐化或不恰当的修改
protections on key systems as well as provide appropriate procedures
入侵检测系统架构
按防护范围分类
基于网络入侵检测系统(NIDS)
passive architecture
installing a network tap, attaching it to a hub,
or mirroring ports on a switch to a N ID S dedicated port.
handle traffic throughput equivalent to (or greater than) the combined traffic load for all the ports on that device,
cannot monitoring encrypted data
Many technologies now exist that can break session encryption
user training and privacy concerns
This can be accomplished in a multitude of ways. For example, it can start blocking any packets coming from the source of the traffic, or it can utilize features of the TCP protocol and inject reset packets into the network, forcing the remote system to cancel the communications. In lieu of directly terminating the session, many ID S solutions can be integrated with firewalls, routers, and switches to facilitate dynamic rule changes to block specific protocols, ports, or IP addresses associated with the unwanted communications.
实时监测网络流量,部署在分接器或交换机的调试端口或集线器上
基于主机入侵检测系统 (HIDS)
实时监控主机审计日志,部署每个关键主机上
limited to the boundaries of a single-host system.
multihost IDSs
identify and respond to data from multiple hosts
share policy information and real time attack
drawback
对主机操作系统侵害性很大
干扰正常系统处理,过度耗费CPU和内存
基于应用IDS
监控具体应用恶意行为的IDS
按防护原理分类
基于特征IDS
特征匹配,类似于防病毒软件
基于签名的IDS
特征必须持续更新
只有先前确定的攻击签名被检测,不能发现新的攻击
分类:特征匹配、状态匹配
基于规则IDS
在专家系统中使用基于规则的程序IF/THEN
允许人工智能
规则越复杂,对软硬件性能要求越高
不能检测新的攻击
基于异常IDS
基于行为的系统,需要学习环境中的“常规”活动
能检测新的攻击
缺点
可能错误得检测出系统中的一个瞬间异常造成的非攻击事件
也叫基于行为或启发式
分类
统计异常
协议异常
流量异常
入侵响应
如果IDS检测到入侵
限制或阻止系统流量
同时也与其他设备集成进行响应
比如将规则注入到路由器、VPN网关、Vlan交换设备等
早期版本的IDS与防火墙集成,指导防火墙对可以流量实施拟定规则
在启动规则的过程中可能会影响正常业务
误报率要严格控制
告警和警报
IDS基本组件
1. Sensor传感器
部署检测机制
识别事件
产生适当提示(notification)
告知管理员
启动某项规则
2 . Control and communication 指挥控制和通信
处理告警信息
发送邮件或文本信息等
3. Enunciator 发布者
中继系统
迅速通知本地资源和远程资源
确定谁能收到信息
保障及时的信息传递机制
确定接收的告警类型以及信息的紧急程度
邮件
短信
IDS管理
IDS为企业广泛采用的安全技术之一
简单投资
不需要或者少量维护
需要大量的维护支持
有效的IDS管理
雇佣一个技术知识渊博的人来选择、实施、配置、运行和维护IDS
定期更新系统新的攻击特征并评价预期行为特征
注意到IDS易受攻击并对其进行有效保护
攻击者可能会发起攻击禁掉IDS/IPS系统
邮件防护——白名单、黑名单和灰名单
白名单
一列被列为“好的”发送者的邮件地址或IP地址等
黑名单
一列“坏”的发送者
灰名单
我不知道你是谁,在我接受之前让你的邮件跳过额外的步骤“
灰名单会告诉邮件发送服务器快速的重新发送新的邮件
非盈利组织
These include the Spamhaus Block List (SBL), the Exploits Block List (XBL), the Policy Block List (PBL), and the Domain Block List (DBL). In addition, Spamhaus maintains The Register of Known Spam Operations (ROKSO) database, which collates information and evidence on known professional spam operations that have been terminated by a minimum of 3 Internet Service Providers for spam offenses.18
非营利组织
追踪互联网垃圾邮件的运营和源头
为互联网提供实时有效的垃圾邮件保护
DLP(Data Leak/Loss Prevention) 数据防泄漏
定义
a suite of technologies aimed at stemming the loss of sensitiveinformation that occurs in the enterprise.
瞄准防止企业敏感信息泄露的一套技术
三个关键目标
1. Locate and catalog sensitive information stored throughout the enterprise. 2. Monitor and control the movement of sensitive information across enterprise networks. 3. Monitor and control the movement of sensitive information on end-user systems.
将存储在整个企业的敏感信息进行定位和编程目录;
对整个企业敏感信息的移动进行监控和控制;
对终端用户系统敏感信息的移动进行监控和控制;
组织敏感信息的分类、存储位置和传输路径
Enterprises are often unaware of all of the types and locations of information they possess.
组织常没有认识到他们处理的信息的类型和位置,购买DLP方案时首先要了解敏感数据类型和系统间以及系统到用户的数据流;
分类Classifications可以包括属性categories,如隐私数据、财务数据和知识产权等;
一旦对数据进行适当的识别和分类,更深的分析流程来帮助进行主要数据和关键数据路径的定位;
需要关注企业数据的生命周期,理解数据的处理、维护、存储和处置等能揭示更深的数据存储和传输路径;
部署DLP的优点
Protect critical business data and intellectual property Improve compliance Reduce data breach risk Enhance training and awareness: Improve business processes Optimize disk space and network bandwidth Detect rogue/malicious software
保护关键业务数据和知识产权;
加强合规;
降低数据泄露风险;
加强培训和意识
改进业务流程;
优化磁盘空间和网络带宽;
检测流氓/恶意软件
Data at Rest静态数据
寻找并识别具体文件类型,识别和记录信息存储的位置;
找到后,DLP打开并识别文件的内容;
DLP使用爬虫系统;crawlers
Data in Motion (Network)动态数据
DLP solution
1. Passively monitor the network traffic 2. Recognize the correct data streams to capture 3. Assemble the collected packets 4. Reconstruct the files carried in the data stream 5. Perform the same analysis that is done on the data at rest to determine whether any portion of the file contents is restricted by its rule set
1、被动的监测网络流量;
2、识别捕获的正确数据流量;
3、组装所收集的数据;
4、在数据流中进行文件重建;
5、执行静态数据同样的分析并确认文件内容任何部分是收到其规则限制的。
为监测企业网络数据移动,DLP方案使用特别的网络设备或内置技术有选择的捕获和分析网络流量;
深度文件检测( deep packet inspection (DPI))技术,作为DLP的核心能力,DPI能够越过基本的包头信息阅读数据包载荷内容
DPI技术允许DLP检测传输中的数据并确定内容、来源和目的地;
DLP有能力应对加密的数据(如具有加密秘钥),或者再检测前进行解密并在检测完成后继续加密;
Data in Use (End Point)使用中的数据
监控终端用户在他们的工作站上所采取数据移动行为
whether that would entail copying data to a thumb drive, sending information to a printer, or even cutting and pasting between applications. 是否需要将数据复制到闪盘、发送信息到打印机甚至是在应用间进行剪切和黏贴;
使用Agent完成任务
DLP Function
策略建立和管理Policy Creation and Management
Policies (rule sets) dictate the actions taken by the various DLP components. Most DLP solutions come with preconfigured policies (rules) that map to common regulations. It is just as important to be able to customize these policies or build completely custom policies. 策略(规则设置)指明不同DLP组件所采取的行动。多数DLP方案伴随预制映射到通用规则的策略。而策略的定制化或建立完全自定义的策略是非常重要的;
集成目录服务Directory Services Integration
Integration with directory services allows the DLP console to map a network address to a named end-user. 集成目录服务允许DLP控制台能将网络地址映射到已命名的终端用户;
工作流管理Workflow Management
Most full DLP solutions provide the capacity to configure incident handling, allowing the central management system to route specific incidents to the appropriate parties based on violation type, severity, user, and other such criteria. 最完整的DLP解决方案能够配置事件处理,允许集中管理系统按照违规类型、严重程度、用户和其他标准将特定的事件指给恰当的部分
备份和恢复Backup and Restore
Backup and restore features allow for preservation of policies and other configuration settings. 备份和恢复功能允许策略和其他配置设置的保护
报告Reporting
A reporting function may be internal or may leverage external reporting tools. 报告功能可能是内部或利用外部工具实现
隐写术和水印技术
cover_medium + hidden_data + stego_key = stego_medium In this context, the cover_medium is the file in which you will hide the hidden_data, which may also be encrypted using the stego_key. The resultant file is the stego_medium (which will, of course, be the same type of file as the cover_medium). The cover_medium (and, thus, the stego_medium) are typically image or audio files.
watermark
隐写术是一种信息隐藏技术,入将大量信息隐藏在图片和视频文件中;
信息隐藏包括隐蔽通道、在Web页面隐藏文本、隐藏可见文件、空密码;
第三方服务、 沙盒、 反恶意软件、 蜜罐系统和蜜网
Third-party Security Services第三方服务
Dynamic application security testing (DAST)
用于检测应用在运行状态中安全漏洞的状态
多数暴露的HTTP和HTML的问题,多基于WEB漏洞
有些为非Web协议和数据畸形
方法
动态应用安全测试是一项服务
具有爬虫能力来测试RIA(Rich Internet Applications)
HTML5.
HTML 5 is not a single standard, and the multiple standards that collectively represent H TML 5 are at different levels of maturity and adoption. Testing HTML 5 and keeping up with the fluid standards is an emerging requirement for all D A ST solutions
具有爬虫能力并测试使用其他Web协议接口的应用
Static application testing capabilities (SAST).
Interactive Security Testing.
Comprehensive fuzz testing
Testing mobile and cloud-based applications.
Honeypots and Honeynets蜜罐系统和蜜网
作为诱饵服务器收集攻击者或入侵者进行系统的相关信息
IDS的变体
更聚焦于信息的收集和欺骗
常见工具
19 http://glastopf.org/ 20 http://www.specter.com/default50.htm 21 https://code. google, com/p/ghost-usb-honeypot/ 22 http://www.keyfocus.net/kfsensor/
Glastopf
ow-interaction,
open source honeypot
Specter -
commercial
Ghost USB
free USB emulation honeypot
KFSensor
Windows based honeypot intrusion detection system (IDS).
Sandboxing沙盒
软件虚拟化技术
让程序和进程在隔离的环境中运行
限制访问系统其他文件和系统
沙盒里发生的只在沙盒里发生
一项取代传统基于签名防病毒
可能检测到零天漏洞和隐藏的攻击
恶意软件会使用各种技术规避检测
Hooks
为检测恶意软件引入的技术
直接插入到程序中得到函数或库调用的通知(call back)
这种技术需要更改程序代码
为恶意软件所感知
打断动态代码的生成
主要问题
在调用时沙盒不能看到恶意软件所执行的任何指令
environmental checks环境监测
Another evasive method is carried out through environmental checks. Malware authors can add novel, zero-day environmental checks related to the operating system and manipulate the return value as an evasive maneuver that forces vendors to patch their sandbox to catch it.
Anti-malware 反恶意软件
Anti-Malware Testing Standards Organization (AMTSO防恶意软件测试标准组织
提供恶意软件测试和相关产品讨论的论坛
发布恶意软件测试的客观标准和最佳实践
促进与恶意软件测试问题有关的教育和意识
提供工具和资源致力于标准化测试和方法
Windows
1. Test if my protection against the manual download of malware (EICAR.COM) is enabled. 2. Test if my protection against a drive-by download (EICAR.COM) is enabled. 3. Test if my protection against the download of a Potentially Unwanted Application (PUA) is enabled. 4. Test if protection against accessing a Phishing Page is enabled. 5. Test if my cloud protection is enable.
1. Test if my protection against the manual download of malware (EICAR.COM) is enabled.
2. Test if my protection against a drive-by download (EICAR.COM) is enabled.
3. Test if my protection against the download of a Potentially Unwanted Application (PUA) is enabled.
4. Test if protection against accessing a Phishing Page is enabled.
5. Test if my cloud protection is enable.
Andorid
1. Test if my protection against the manual download of malware is enabled. 2. Test if my protection against a drive-by download is enabled. 3. Test if my protection against the download of a Potentially Unwanted Application (PUA) is enabled. 4. Test if protection against accessing a Phishing Page is enabled.
灾备
制定恢复策略
Recovery strategies are driven by the recovery time frame required by the function or application to be recovered.
需要考虑的恢复策略
Surviving Site存活站点
A surviving site strategy is implemented so that while service levels may drop, a function never ceases to be performed because it operates in at least two geographically dispersed buildings that are fully equipped and staffed
Self-Service自助服务
An organization can transfer work to another of its own locations, which has available facilities and/or staff to manage the time sensitive workload until the interruption is over.
Internal Arrangement 内部安排
Training rooms, cafeterias, conference rooms, etc. may be equipped to support organization functions while staff from the impacted site travels to another site and resumes organization.
Reciprocal Agreements/Mutual Aid Agreements 互惠协定/互助协定
Other similar organizations may be able to accommodate those affected. For example, one law firm may be able to provide office space to another in the event of an outage. This could involve the temporary suspension of non-time sensitive functions at the organization operations not affected by the outage
Dedicated Alternate Sites 专用备用站点
Built by the company to accommodate organization function or technology recovery.
Work from Home 在家上班
Many organizations today have the capability to have employees work from locations that are remote from a physical office environment.
External Suppliers 外部供应商
A number of external organizations offer facilities covering a wide range of organization recovery needs from full data centers with a wide range of platforms, alternate site space in physical facilities, mobile units that can be transported to the company site, and temporary staff to provide services when the employees cannot.
No Arrangement 没有布置的
For low-priority business functions or applications, it may not be cost justified to plan at a detailed level. The minimum requirement would be to record a description of the functions, the maximum allowable lapse time for recovery, and a list of the resources required.
恢复策略的选择必须符合组织需求
成本效益分析 (CBA)
建立策略的初始费用
维护恢复策略解决方案的持续费用
方案定期测试的费用
通信相关的费用
实施备份存储策略
恢复时间目标 (RTO)\最大容忍宕机时间 (MTD) \ 恢复点目标 (RPO)
Some organizations have begun tiering data based on its importance to the organization and frequency of use. The more time sensitive data is replicated offsite either synchronously or asynchronously to ensure its availability and its currency.
备份方法
全备
增量备份
take copies of only the files that have changed since the last full or incremental backup was taken
and then set the archive bit to “0.”
takes the most time in restoration
差异备份
copies only the files that have had their data change since the last full backup
since the last full backup and does not change the archive bit value.
恢复站点策略
Dual Data Center双数据中心
The applications are split between two geographically dispersed data centers and either load balanced between the two centers or hot swapped between the two centers. The surviving data center must have enough head room to carry the full production load in either case.
使用该战略使得应用不能接受宕机影响组织
优势
停机时间较少或没有
易于维护
无需恢复
缺点
费用较高
需要冗余硬件、网络和人员
受限于距离
hot sites热战
Internal Hot Site 内部热站
The administrator will be able to effectively restart an application in a hot site recovery without having to perform any bare metal recovery of servers. If this is an internal solution, then often the organization will run non-time sensitive processes there, such as development or test environments, which will be pushed aside for recovery of production when needed. When employing this strategy, one must keep the two environments as close to identical as possible to avoid problems with O/S levels, hardware differences, capacity differences, etc. from preventing or delaying recovery.
准备具有运行应用程序所需的所有的技术和设备的待机站点
run non-time sensitive
例如开发或测试环境
External Hot Site外部热站
This strategy has equipment on the floor waiting, but the environment must be rebuilt for the recovery.
设施已经就位,但是环境需要重建
这些服务于服务提供商协定
Again, it is important that the two environments be kept as close to identical as possible to avoid problems with O/S levels, hardware differences, capacity differences, etc. from preventing or delaying recovery. Hot site vendors tend to have the most commonly used hardware and software products to attract the largest number of customers to utilize the site. Unique equipment or software would generally need to be provided by the organization either at time of disaster or stored there ahead of time.
优势
允许测试恢复策略
高可用性
站点可在数小时内恢复
缺点
内部热站比外部热站更贵
外部热站存在软硬件兼容问题
Warm Site 温站
A leased or rented facility that is usually partially configured with some equipment but not the actual computers. It will generally have all the cooling, cabling, and networks in place to accommodate the recovery, but the actual servers, mainframe, etc. equipment are delivered to the site at the time of disaster.
部分配置有一些设备但不是真实的计算机的租赁设施
Cold Site 冷站
冷站就是一个壳或空数据中心,且地板上没有任何技术设施
All technology must be purchased or acquired at the time of disaster.
优势
低成本
用于较长的恢复
缺点
不能及时恢复
没有前期完全的测试工作
mobile site 移动站点
是内部配置适当电信装备和IT设备的可移动拖车或标准的集装箱, 可以被机动拖放和安置在所需的备用场所,提供关键的应用服务,如电话交换功能等。
优点
高机动性以及相对容易运输
模块化方法构建数据中心
构建时不需要室内设备
缺点
冷站能力必须在指定位置建立
容器的密度和设计使得升级和定制化受到极大得挑战
维持在灾难时的航运合同或或移动设备非常昂贵
多处理数据中心
如果组织的设施覆盖全国或全世界可以使用此解决方案
具有足够的带宽和延迟
可以认为组织内部的“互惠协议”
处理协议
Reciprocal agreements 互惠协议
组织间用来分享宕机风险
在灾难发生时,每个组织承诺承担彼此的数据和处理任务
问题
组织承诺为他人保留空余处理能力或在其他组织宕机时降低处理能力
首先需要组织能够遵守这些协议
在行业内或竞争对手间很难找到合适的合作伙伴
outsourcing 外包
符合企业的成本效益需求
承担未知能力以及能够符合要求的风险
SAL协议能表明在一段时间内提供服务,但不能真正保障在灾难时提供保障
优点
按需服务
所有要求和执行责任都在第三方
较少的成本
提供更广的地域选择
缺点
更多主动测试和评估来确认能力保持情况
协议争论使得厂家不能执行
如果部署私有系统将锁定厂商
如果频繁发生中断可能能力构建的费用更多
系统韧度和容错要求
可信路径和故障安全机制
可信路径
为特权用户功能提供可信接口
提供确保使用该路径的通信不会被拦截或破坏的方法
Typical countermeasures
log collection and analysis, vulnerability scanning, patch management, and system integrity checking on a regular basis
Fail-Safe故障保障
发生故障时自动开启(如电源中断)
关注生命或系统安全
Fail-Secure 故障财物安全
发生故障时自动锁闭(如电源中断)
关注故障后以可控的方式阻止访问,当系统处于不一致状态时
冗余和容错
设备备份
备件
冷备用
A cold spare is s a spare component that is not powered up but is a duplicate of the primary that can be inserted into the system if needed.
备件没有启动
和主设备一模一样
如果需要可以使用
一般在存储在主设备附近
不能用于非人工环境
暖备用
已经注入系统但是没有启用,除非有需要
热备用
注入系统并开机直到需要时唤醒
冗余系统
典型的冗余配置
主备对模式
主系统提供所有服务
被动系统监控主系统的问题
集群
两个或多个加入集群并同时提供服务
电源备份
冗余(或双)电源供给
UPS)
替代能源(如柴油发电机)
驱动器和数据存储
SAN和NAS
SAN存储区域网络
A SAN consists of dedicated block level storage on a dedicated network.
numerous storage devices such as tape libraries, optical drives, and disk arrays
protocols like iSCSI to appear to operating systems as locally attached devices
large banks of disks are made available to multiple systems connecting to them via specialized controllers or via Internet Protocol (IP) networks
NAS网络附加存储
file level instead of the block level
designed to simply store and serve files
FTP servers
共享文件服务器
网络驱动器
NAS may also be used to provide storage for multiple systems across the network.
RAID 廉价冗余磁盘阵列
用于提高冗余和或性能改进的技术,以逻辑的方式结合多个物理磁盘形成逻辑阵列。当数据别保存时,信息会写入所有的驱动里
RAID 0
Writes files in stripes across multiple disks without the use of parity information.
fast reading and writing
all of the disks can be accessed in parallel.
does not provide redundancy
use RAID 0 to store temporary data
RAID 1
This level duplicates all disk writes from one disk to another to create two identical drives.
data mirroring.
Redundancy
costly
RAID 2
This R A ID level is more or less theoretical and not used in practice.
Hamming error correction code
RAID 3 and 4 -
These levels require three or more drives to implement.
get striping of data
parity drive
Parity information
written to a dedicated disk
Data is striped
across multiple disks at the byte level for RAID 3 and at the block level for RAID 4.
致命弱点
parity drive
parity drive is the Achilles’ heel because it can become a bottleneck and will typically fail sooner than the other drives.
RAID 5
is similar to RAID 4
parity information is striped together across all drives
most commonly used for general data storage.
RAID 6
extends the capabilities of R A ID 5
computing two sets of parity information.
the performance of this level is slightly less
RAID 0+1 and RAID 1+0 -
In R A ID 0+1, two different arrays of disk are at play. The first set of disks stripes all of the data across the available drives (the R A ID 0 part) and those drives are mirrored to a different set of disks (the R A ID 1 part). In R A ID 1+0 (also known as R A ID 10), two different arrays of disk are at play,. When data is striped to one drive, it is immediately striped to another. In general, R A ID 1+0 is considered to be superior to R A ID 0+1 in all respects, both in terms of speed and redundancy
combining two different R A ID types
冗余独立磁带阵列 (RAIT).
database shadowing
用于数据库管理系统在多点的记录更新
用于远程的完整数据库拷贝
备份和恢复系统
Backup and recovery systems focus on copying data from one location to another so that it can be restored if it is needed
备份数据包括关键系统文件和用户数据
备份窗口
足够大
全备
不足够大
差备或增量备份
备份涉及生产系统拷贝数据到远程介质中
如将高密度磁带传输或存储到不同的地方
至少三个备份磁带
原站点
恢复单个故障系统
近站点
used only when the primary facility has suffered a more general failure and where the local tapes have been damaged
主站点遭受了普遍故障,且磁带已损坏
远程站点
异地站点
This provides assurance of a recovery in the event that the facility is destroyed in a catastrophe. The off- site location should be far enough away to preclude mutual destruction in the event of a catastrophe but not so far away as to introduce difficulties in transporting the media or retrieving it for recovery purposes. Unfortunately, the answer to offsite storage is a difficult challenge in areas prone to natural catastrophes.
离主站点的有段距离的安全位置
电子传送
通过网络备份数据
实现镜像
主系统的变更实时传送到库服务器中
存储库服务器
配置成类似于存储设备
与实时更新相反,文件的变更使用增量和差异备份方式传递到存储库
日志或交易记录
数据库管理系统使用的技术提供交易的冗余
When a transaction is completed, the database management system duplicates the journal entry at a remote location. The journal provides sufficient detail for the transaction to be replayed on the remote system. This provides for database recovery in the event that the database becomes corrupted or unavailable
人员编制弹性
An important part of maintaining resilient operations is ensuring adequate and trained staff is available to keep everything running smoothly.
避免关键人员的单点失败
足够的人员配备水平
适当的培训和教育
轮岗培训
灾难恢复流程
DR areas
DR包括反应、人员、沟通、评估、恢复和培训
过程必须记录.
组织级的持续测试策略
the board and senior management
测试策略和计划
包括使用BIA和风险评估
识别关键角色和职责,建立组织业务连续性测试的最小要求,包括测试频率、范围和结果报告的基线要求
测试策略的变化依赖于组织的范围和风险场景
处理组织及其服务提供商的测试问题
内部系统的测试策略应在系统和数据文件被测试时包含所涉及的人员
计划文档化
记录应对各种事件的恢复
文档应存储在所有的恢复设施里
文档对技术恢复操作要足够详尽,有相关技能的人,首次执行仍可完成
每次测试恢复计划,根据需要进行更新
响应
事件发生后通报给集中通信团队
集中的号码
帮助服务台
技术操作中心
物理安全人员
监控人员
响应计划
建立紧急联系名单
评估团队
首先通知
确定事件是否需要升级
首个升级团队
The first escalation team consists of the event owner, the event responders, and anyone else who has determined that when this type of disruption occurs, it directly and immediately affects their ability to execute the business or mission performed in that environment.
事件所有者
事件响应者
建立通信渠道
conference call
They communicate what the problem is, the current status of the problem, how long it should be before it is resolved, what is impacted, and if necessary, when the next update will be provided and how.
建立内外部的可替代通信渠道
不要忘记一些服务的不可用
快递
水电服务
高管应急管理团队
由组织中的高级管理人员组成
不需要做作为初始响应的部分
为组织和业务的恢复负有全责
事件发生后位于指令中心
不需要管理日常运维
高管需要响应和协助需要他们指导的问题的解决
关注战略响应
Crisis Managemen t vs. Crisis Leadership
Managing
响应
短期
流程
狭窄
战术层次
Leading
期望
长期
原则
广泛关注
战略层次
应急管理团队
直接向指令中心汇报
具有监控灾难恢复团队,制定恢复和复原流程的职责
向高管汇报事件状态
制定支持恢复的决策
主要职能
■ Make a preliminary assessment of the damage. ■ Notify senior management on the current status, impact to organization, and plan of action. ■ Declare the disaster if necessary. ■ Initiate the plan during the emergency situation. ■ Organize and control the command centers as a central point of control of the recovery efforts. ■ Organize and provide administrative support to the recovery effort. ■ Administer and direct the problem management function.
灾难恢复团队
检索异地记载和异地存储的恢复信息
向异地站点报告
按优先级顺序执行恢复过程
按需向指挥中心沟通恢复情况
识别问题,并报告给管理团队以获取解决方案
建立恢复团队支持7*24小时全天候的班次
建立关键业务用户和人员联络
修复更换设备和必要的软件来恢复正常运营
指令中心
在紧急状况中用于通信和决策的中心
在灾难中,用于响应灾难配备应急响应文档以及其他所需资源
也包含处理财物问题的程序
初始响应计划
组织具有多个位置,则需要为每个业务站点准备一个计划
站点中有哪些关键业务或技术
为其准备恰当的恢复策略
谁是决策者
如果不能回到建筑物内,人们应该去哪
宣告灾难发生的流程
备份站点的位置
到达备份站点的差旅方式
备份站点的工位分配
备份站点附近的酒店\交通服务和后勤服务
人事
很多计划的问题就是人力资源问题
灾难能够极大的影响到人员
灾难中组织在响应自己的需求外还需要关注相应团队家庭的艰难状况
支持团队成员的水平将由灾难本身的性质明确界定
将行政支持作为恢复团队的一部分
They do things no one else has the time to do - answering phones, sending communications as requested to communicate to recovery staff, making travel arrangements for recovery staff, ordering food at recovery locations, keeping minutes of the status meetings, making copies, arranging courier service, keeping track of the locations of employees, and similar administrative and personnel related functions
沟通
通知员工
在紧急状况中由责任管理团队直接联系应急联系名单中的成员
描述组织如何联系剩余成员
建立应急信息线
让员工了解发生的灾难信息
放在员工的工牌后面、冰箱贴
利益相关者
Employees and their families
Contractors and business partners
Q Facility and Site Managers
Q Staff Managers (HR, IT, etc.)
Q Senior Managers; Board of Directors
Institutional investors and shareholders
Insurance representatives
Suppliers and Distributors
Customers
Goverment Regulators and Politicians
Competitors
Unions
Communities
Industry activist groups
Internet users or bloggers
Media representatives
如何去说
Employees may be worried about their jobs, where stockholders may be more worried about the impact to the company stock, and customers just want to know that their product or service will be there when they need it.
在灾难恢复过程中,每个员工应向客户或厂商说的状况是一致的
企业应向所有利益相关者提供恢复状态的最新信息
诚实
精确
安全专家需要建立问题报告和管理流程
conference bridges
评估
在事件中,需要确定事件的影响
tiers or categorizations
Non-Incident 非事件
These events are typically caused by system malfunctions or human errors, which result in limited to minor disruptions of service. There is a short period of downtime and alternate processing or storage facilities are not required.
Incident 事件
Events that cause an entire facility or service to be inoperative for a significant amount of time. These events require the enactment of the disaster recovery plan and reporting of information and status to senior management and may involve crisis management.
向管理层报告
Severe Incident 严重事件
Significant destruction or interruption to an organizations mission, facility, and personnel. These events require the enactment of the DR plan and may involve the building of a new primary facility. These events require senior management reporting and crisis management.
需要管理层报告
恢复
计划中最后一部分是关于主环境复原以及迁移到正常运行
组织的其他部分关注与备用站点组织的复原
部分关注恢复到主设施生产环境所需要做的事情
复原主站点前需要联系法律部门和保险公司
在采取行动前拍照
迁移计划必须记录如何迁移的流程以及操作的细节
For example, an organization may be located in alternate sites for 15 months following the events of an earthquake and for two months following the events of a hurricane. After 9 weeks in the earthquake alternate site, an interim transition plan was executed where employees were distributed between two interim sites while the primary site was repaired and built out.
资产替换
与厂商协商提供设备构建或复原数据中心
提供培训
不管计划多好如果没人知道就不起作用
领导团队
知道危机管理
在灾难恢复中不是执行恢复而是领导组织回归正常
技术团队
知道执行恢复的程序
以及他们要去的后勤设施
雇员
撤离计划
将一部分BCP计划放到新人培训中
演练、评估和维护计划
testing strategy
■ Expectations for business lines and support functions to demonstrate the achievement of business continuity test objectives consistent with the BIA and risk assessment; 业务线和支持职能部门展示业务连续性性测试目标获得的期望,符合BIA和风险评估
■ A description of the depth and breadth of testing to be accomplished; 完成测试的深度和广度的描述
■ The involvement of staff, technology, and facilities; 员工、技术和设施的范畴
■ Expectations for testing internal and external interdependencies; 内外依存度测试期望
■ An evaluation of the reasonableness of assumptions used in developing the testing strategy. 评价在开发测试策略中臆测的合理性
测试策略包含测试目标和范围
define what functions, systems, or processes are going to be tested and what will constitute a successful test
BCP每年至少测试一次
当重大变更发生时需要进行测试
测试目标刚开始可以简单逐渐增加复杂度、参与级别、职能以及物理位置
测试不要危及正常业务运行
测试展示在模拟危机下各种管理和响应能力,逐渐增加更多的资源和参与者
揭示不恰当之处以便修正测试程序
考虑偏离测试脚本插入意外事件,比如关键个人或服务的损失
包括足量所有类型交易确保恢复设施适当的能力和功能
测试策略包含测试计划
基于预定的测试范围和目标
包含测试计划评审程序
包含各种测试场景和方法的开发
测试计划
主测试计划应包括所有的测试目标
测试目标和方法的具体描述
所有测试参加者包括支持人员的角色
测试参与者的委派
测试决策制定者和后续计划
测试位置
测试升级条件和测试联系信息
测试计划评审
测试战略
测试范围和目标
BIA,验证RTO和RPO
测试策略
由高层制定
角色职责,频率、范围和报告结果
业务恢复和灾难恢复练习
business recovery
关注测试业务线的运行
disaster recovery
关注技术部分连续性的测试
检查清单评审
BCP拷贝分发给每个关键业务部门的经理
请求他们评审适合他们部门的计划部分
桌面演练/结构化演练测试
作为计划初始测试的工具,但不是最好的测试方法
目标
确保来自所有领域的关键人员熟悉BCP
确保计划反应组织从灾难恢复过来的能力
特点
■ Attendance of business unit management representatives and employees who play a critical role in the BCP process; ■ Discussion about each person’s responsibilities as defined by the BCP; ■ Individual and team training, which includes a walk-through of the step-bystep procedures outlined in the BCP; and ■ Clarification and highlighting of critical plan elements, as well as problems noted during testing.
会议室联系,低成本
排演演练/模拟演练
■ Attendance by all operational and support personnel who are responsible for implementing the BCP procedures; ■ Practice and validation of specific functional response capabilities; ■ Focus on the demonstration of knowledge and skills, as well as team interaction and decision-making capabilities; ■ Role playing with simulated response at alternate locations/facilities to act out critical steps, recognize difficulties, and resolve problems in a nonthreatening environment; ■ Mobilization of all or some of the crisis management/response team to practice proper coordination without performing actual recovery processing; ■ Varying degrees of actual, as opposed to simulated, notification and resource mobilization to reinforce the content and logic of the plan.
比桌面演练包含的内容更多
参加者选择具体的事件场景应用在BCP中
功能性测试/并行测试
包含真实人员移动到别的站点力图按照BCP规定建立通信和实施真实的恢复流程
主要是确定如果人员应用BCP规定中的程序,关键系统是否能够在备用处理站点恢复
特点
■ A full test of the BCP, which involves all employees; ■ Demonstration of emergency management capabilities of several groups practicing a series of interactive functions, such as direction, control, assessment, operations, and planning; ■ Testing medical response and warning procedures; ■ Actual or simulated response to alternate locations or facilities using actual communications capabilities; ■ Mobilization of personnel and resources at varied geographical sites, including evacuation drills in which employees test the evacuation route and procedures for personnel accountability; and ■ Varying degrees of actual, as opposed to simulated, notification and resource mobilization in which parallel processing is performed and transactions are compared to production results.
完全中断/全面测试
■ Enterprise-wide participation and interaction of internal and external management response teams with full involvement of external organizations; ■ Validation of crisis response functions; ■ Demonstration of knowledge and skills as well as management response and decision-making capability; ■ On-the-scene execution of coordination and decision-making roles; ■ Actual, as opposed to simulated, notifications, mobilization of resources, and communication of decisions; ■ Activities conducted at actual response locations or facilities; ■ Actual processing of data using backup media; and ■ Exercises generally extending over a longer period of time to allow issues to fully evolve as they would in a crisis and to allow realistic role-playing of all the involved groups.
最复杂的测试
尽可能模拟真实的场景
不能影响业务
更新和维护计划

任何团队都有义务参与变更控制流程
计划文档和所有相关程序每三个月检查一次
程序的正式审计每年至少一次
计划必须控制版本
从项目到方案
连续性计划方案是正在进行的流程
所有定义的任务都要与时俱进与现有环境保持一致
必须要有年度要求

emergency management organization (EMO) 应急管理组织
正式的管理层响应流程
现场覆盖、支持和专业知识
涉及的领域
■ Security
■ Real estate
■ Systems
■ Human resources
■ Organizational communications
■ Compliance
■ Risk and insurance management '
■ Organizational contingency planning
团队的职责
■ Responding to incidents and emergencies
■ Determining the extent of the impending or actual emergency situation
■ Establishing and maintaining communication with senior management
■ Communicating with employees and customers
■ Managing media communications, security, systems, facilities
■ Coordinating and integrating business continuity planners
The organizational emergency operations center (EOC)
提供位置
不管EMO是否启动提供必要的资源管理组织的恢复
Roles and Responsibilities 角色和职责
The organizational contingency planning group
■ Setting strategic direction and plans for all organization units to ensure BC and effective emergency management.
■ Integrating the contingency planning process across organization units when the nature of the organization requires it.
■ Providing consulting services and direction to senior level contingency managers.
■ Coordinating and integrating the activation of emergency response organizations with the organization units.
■ Providing periodic management reporting and status.
■ Ensuring executive management compliance with the contingency planning program.
■ Ensuring the identification and maintenance of all critical organization functions and requirements.
■ Procuring and managing the alternate sites used to support recovery of the operations of the company whether technical or organization.
■ Developing, implementing, and maintaining policy and guidelines for all organization units to follow.
■ Developing and maintaining testing and maintenance programs for all contingency planning organizations.
■ Providing training, maintenance, and support for approved contingency planning tools.
business continuity planners
■ Provide primary contact for their functional area to handle coordination response during an organization interruption.
■ Act as a resource for contingency planning efforts within their area of responsibility.
■ Secure appointment, training, and backup of all contingency planning and response teams.
■ Assist in the design and maintenance of alternate sites.
■ Maintain currency of all contingency planning documentation, including all deliverables listed in Figure 7.8.
 
■ Program Requirements
业务连续性和其他风险域
BC和其他安全域有非常重要的关系
physical security, records management, vendor management, internal audit, financial risk management, operational risk management, and regulatory compliance (legal/regulatory risk) in the context of an overall risk management framework.
物理访问控制
The primary function of an access control system (ACS) is to ensure that only authorized ersonnel are permitted inside the controlled area.
边界安全的实施和运行
物理安全的目的
控制对物理设施的访问,设施防护的第一道屏障
深度防御 defense-in-depth
 
如果一层机制失败,其他机制起作用
secure the weakest link 保护最弱环节
“rings of protection
阻止-检测-延迟-响应deter-detect - delay-respond
Deter is meant to render a facility as an unattractive target so that an adversary abandons attempts to infiltrate or attack Detect involves the use of appropriate devices, systems, and procedures to signal that an attempted or actual unauthorized access has occurred Response requires communication to a response force that an unauthorized person is attempting to or has entered the facility.
建筑物关键组建示例
■ Emergency generator, including fuel systems, day tank, fire sprinkler, and water supply应急发电机
■ Fuel storage燃料库
■ Telephone distribution and main switchgear
■ Fire pumps 消防泵
■ Building control centers楼宇控制中心
■ Uninterrupted power supply (UPS) systems controlling critical functions
■ HVAC systems if critical to building operation
■ Elevator machinery and controls 起重机械和控制
■ Shafts for stairs, elevators, and utilities 楼梯井、电梯和工具
■ Critical distribution feeders for emergency power
门和墙
Barriers 屏障
Barriers can be comprised of natural or manufactured elements,如山、河、绿化带
is designated to impede or deny access.
objective
Keep intruders out, delay them, and keep them at a safe distance
Fences 围栏
fences are a perimeter identifier that is designed and installed to keep intruders out.
the chain linked fence
The standard is a six-foot high fence with two-inch mesh square openings. consist of nine-gauge vinyl or galvanized metal 
largely a psychological deterrent
a boundary marker
Gates门
Gates exist to facilitate and control access.
Walls 墙壁
Walls serve the same purpose as fences
walls ought to be 7 feet high with 3 to 4 strands of barbed wire on top
边界入侵检测
Infrared Sensors 红外传感器
Active infrared sensors
transmit an infrared signal via a transmitter.
The location for reception is at a receiver.
Interruption of the normal IR signal indicates an intruder or object has blocked the path
Passive infrared sensors
Passive infrared sensors are designed for human body detection, so they are great for detecting when someone approaches.
Passive-infrared sensors detect the heat emitted by animate forms
Microwave 微波
two configurations
bistatic and monostatic 双基或单基
radiating a controlled pattern of microwave energy into the protected area.
The transmitted microwave signal is received, and a base level “no intrusion” signal is established
bistatic sensor
 
sends an invisible volumetric detection field that fills the space between a transmitter and receiver.
Monostatic microwave sensors
use a single sensing unit that incorporates both transmitting and receiving functions.
Coaxial Strain-Sensitive Cable 同轴应变敏感电缆

These systems use a coaxial cable woven through the fabric of the fence
The coaxial cable transmits an electric field
Time Domain Reflectometry (TDR) Systems 时间域反射器(TDR)系统
Time Domain Reflectometry (TDR) systems send induced radio frequency (RF) signals down a cable that is attached to the fence fabric.
Intruders climbing or flexing a fence create a signal path flaw that can be converted to an alarm signal
Video Content Analysis and Motion Path Analysis 视频内容分析和运动路径分析

is sophisticated software analysis of the camera images.
CCTV camera systems are increasingly being used as intrusion detection systems.
使用复杂算法允许CCTV系统来检测入侵者
光照
Lighting should enable security personnel and employees to notice individuals at night at a distance of 75 feet or more and to identify a human face at about 33 feet.
Security lighting can be provided for overall facility illumination along with the perimeter to allow security personnel to maintain a visual assessment during times of darkness.
provide both a real and psychological deterrent
Types of Lighting Systems
Isolation zones and all exterior areas within the protected area shall be provided with illumination sufficient for the monitoring and observation requirements, but not less than 0.2 fc measured horizontally at ground level. 0.5 fc is acceptable for side landscapes and roadways.
Continuous lighting 连续照明
Continuous lighting is the most common security lighting system. It consists of a series of fixed lights arranged to flood a given area continuously during darkness with overlapping cones of light.
Standby lighting 备用照明
Standby lighting has a layout similar to continuous lighting; however, the lights are not continuously lit but are either automatically or manually turned on when suspicious activity is detected or suspected by the security personnel or alarm systems.
Movable lighting 流动灯光
Movable lighting consists of manually operated, movable searchlights that may be lit during hours of darkness or only as needed. The system normally is used to supplement continuous or standby lighting.
Emergency lighting 应急灯光
Emergency lighting is a backup power system of lighting that may duplicate any or all of the above systems. Its use is limited to times of power failure or other emergencies that render the normal system inoperative. It depends on an alternative power source such as installed or portable generators or batteries. Consider emergency/backup power for security lighting as determined to be appropriate.
0.2 foot-candles
Types of Lights
Fluorescent lights 荧光灯
Fluorescent lights are highly efficient and cost effective. However, they are temperature sensitive and while improving are not considered an effective outdoor lighting system. This light is better suited inside buildings and facilities.
Mercury vopor lights 汞蒸气灯
Mercury vopor lights are the preferred security light that disperses a strong white-bluish cast. They have an extended lamp life; however the downside is hey take an amount of time to full light when activated - typical to the lights at a stadium.
Sodium vopor lights 钠蒸汽灯
Sodium vopor lights provide a soft yellow light and is more efficient than mercury vapor. This light is used in areas where fog can be a problem.
Quartz lamps 石英灯
Quartz lamps emit a very bright white light and comes on immediately. They typically provide high wattage from 1500 to 2000 and can be used on perimeters and troublesome areas where high visibility and a daylight scene is required.
American Institute of Architects
interior lighting levels
range from 5 to 10 fc;
exterior lighting requirements
■ Building entrances (5 fc)
■ Walkways (1.5 fc)
■ Parking garages (5 fc)
■ Site landscape (0.5 fc)
■ Areas immediately surrounding the building (1 fc)
■ Roadways (0.5 fc)
Adequate lighting for monitoring activities is important.
Lights used for CCTV monitoring generally require at least 1 to 2 fc of illumination, whereas the lighting needed for safety considerations in exterior areas such as parking lots or garages is substantially greater (at least 5 fc).
Infrared Illuminators 红外照明
Most monochrome CCTV
invisible infrared light can be used to illuminate a scene, which allows night surveillance without the need for additional artificial lighting. 
卡的类型
磁条卡
consist of a magnetically sensitive strip fused onto the surface of a PVC material, like a credit card. 
在PVC材料上附有敏感词条,如信用卡
感应卡
Proximity cards (prox cards) use embedded antenna wires connected to a chip within the card. The chip is encoded with the unique card identification. Distances at which proximity cards can be read vary by the manufacturer and installation. Readers can require the card to be placed within a fraction of an inch from the reader to six inches away. This will then authenticate the card and will release the magnetic lock on the door.
内置天线,天线挎包姐着具有识别码的芯片,阅读器可通过磁场来阅读芯片的内容
智能卡
Smart cards are credential cards with a microchip embedded in them
含有微处理芯片的IC卡,具有一定的数据处理能力
可以集成其他安全措施
带有PIN码的按键或生物识别措施
CCTV闭路电视
功能
Surveillance监督
CCTV cameras can be used to give a viewer the capability to be made aware of or view visual events at multiple locations from a centralized remote viewing area. CCTV camera technology makes visual information available that would normally only be available through multiple (possibly roving) human resources.
Assessment 评估
When alerted by an alarm notification, CCTV cameras allow the security control center operators or other viewers to assess the situation and make a determination as to what type of response may or may not be required. An example would be an intrusion alarm at a remote facility. Visual assessment may indicate an unannounced maintenance crew at work. This situation will be handled differently than if the operator viewed an unknown individual removing a laptop from the facility.
Deterrence 威慑
While more effective against unsophisticated burglars, as opposed to trained covert insurgents, CCTV cameras may deter burglary, vandalism, or intrusion due to fear of discovery and prosecution.
Evidentiary Archives证据归档
Retrieval of archived images may be helpful in the identification and prosecution of trespassers, vandals, or other intruders.
摄像头
Color cameras offer more information,
Some ultra-low-light color cameras are able to automatically sense the ambient light conditions and switch from color to black and white in low-light conditions. Black and white cameras are more sensitive under low-light or darkness conditions Color cameras require a higher illumination level than black and white cameras to be effective.
Outdoor camera户外摄像机
Outdoor camera installations cost more than indoor cameras due to the need to environmentally house, heat, and ventilate the camera
Fixed Position Cameras 固定位置摄像机
Fixed cameras are good for review of pre-alarm conditions because there is a static view of the alarm area. Pre-alarm allows the review of video information for the time period immediately before the alarm occurred
A fixed position camera cannot rotate or pan
Pan/Tilt/Zoom (PTZ) Cameras 平移/倾斜/变焦(PTZ)相机
 
PTZ camera mounts allow the camera to rotate, pan, tilt, and zoom
Dome Cameras 半球摄像机
Dome cameras (Figure 7.17) are actually a cheaper version of the PTZ camera when the total cost is considered (installation, parts, and maintenance).
Internet Protocol (IP) Cameras
An IP camera captures a video image digitally
The IP camera resides on a local area network
Lens Selection
Focal length is the distance from the surface of the lens to the point of focus measured in millimeters.
Focal lengths of most CCTV camera lenses vary from 3.6mm to 16mm for fixed focal length lenses to well over 70mm for zoom lenses. For a security camera in a warehouse with a high visibility requirement, a 2.8 or 4mm lens (makes wide, somewhat distant view) is the best choice. If the requirement is to positively identify people 25 feet away from a camera, a short focal length lens, 3.6mm, would give such a large field of view (37 feet x 26 feet) that recognition would be uncertain. An 8mm or even 12mm lens would be far better (see Figure 7.18).
Lenses either have a fixed or variable focal length
Lighting Requirements
One design parameter of CCTV systems is specification of a proper light-to-dark ratio in the space viewed. “
“Light-to-dark” ratio
“Light-to-dark” ratio refers to the light intensity (as measured in foot-candles or LUX) of the lightest (most reflective surface) to the darkest (least reflective surface). When the ratio is too high, the shadows appear black and the viewer cannot distinguish any shapes in the shadows.
Resolution分辨率
图像的分辨率
Frames Per Second (FPS)
Additionally, CCTV cameras have the option to transmit video at two image rates: alarm condition and non-alarm condition. Making use of a lower non-alarm fps can reduce project cost by allowing a lower bandwidth transmission and storage recording of the CCTV system.
每秒帧
frames per second (fps).
CCTV cameras transmit video in image frames
Compression 压缩
Digital images and digital video can be compressed in order to save space on hard drives and make transmission faster.
MPEG-4.
Digital Video Recorder (DVR)数字硬盘录像机
DVR is used principally for the download of camera images onto a hard drive for recording nd storage of historical information.
DVRs typically come in an 8 port or 16 port version, meaning that 8 or 16 cameras can be recorded at one time
监控显示屏

Single Image Display 单个图像显示
Split Screen 分屏显示
Matrix Displaying for Large Format Displays 显示大型格式显示矩阵
LCD and flat-screen plasma displays (Figure 7.19) lend themselves to programming to show several camera images. The configuration is best done in a square matrix
报警
监控中心

also known as the security console center
dispatch center
Maintaining a 24/7 security control center requires at the minimum two officers per shift.
设计需求
The control center will be located on the main floor or in the basement of the facility, as long as the area is not below ground level and there is no chance of flooding Entry will be controlled, and only authorized personnel will be allowed inside the center. The control center will be provided with primary and secondary sources of power. The secondary power should consist of a battery backup or UPS system that will provide for a normal load of at least 24 hours. It is also recommended that an engine drive generator system be used as a complement to the rechargeable battery system in order to keep uninterrupted power to the control center.
门卫
物理保护措施最终都需要人员介入响应报警
安全人员恶意对建筑物进行足部巡逻,或驻足于某一固定位置
通过检查员工的身份识别卡控制访问
威慑力强,但成本高
人员可靠性有限
Contract security can adapt staffing levels more easily than a proprietary system, as the need for staff rises and falls due to sudden or unexpected circumstances Contract security employees are seen as impartial because they are paid by an outside company to enforce a set of policies and are not as likely to deviate from procedures due to personal relationships or pressure.
选择保安时进行筛选,选择可靠的人员比较重要
Proprietary
The advantages of proprietary security include the quality of personnel, degree of control over the security program, employee loyalty to the company, and prestige for both the employee and the company
Proprietary guards benefit from esprit de corps and a sense of community
disadvantages
including cost, administration, staffing, impartiality, and expertise
Hybrid
allows an organization to maintain more control over its security program while achieving the cost savings and administration reduction associated with contract security
内部安全
内部入侵检测系统
Balanced Magnetic Switch (BMS) 平衡磁开关
This device uses a magnetic field or mechanical contact to determine if an alarm signal is initiated. 
Motion Activated Cameras 动态激活摄像机
A fixed camera with a video motion feature can be used as an interior intrusion point sensor. In this application, the camera can be directed at an entry door and will send an alarm signal when an intruder enters the field of view.
Acoustic Sensors 声学传感器
This device uses passive listening devices to monitor building spaces. An application is an administrative building that is normally only occupied in daylight working hours.
Infrared Linear Beam Sensors 红外线光束传感器
Many think of this device from spy movies, where the enduring image of secret agents and bank robbers donning their special goggles to avoid triggering an active infrared beam is recalled
Passive Infrared (PIR) Sensors 被动红外传感器
A PIR sensor (Figure 7.23) is one of the most common interior volumetric intrusion detection sensors. It is called passive because there is no beam.
Dual-Technology Sensors
These provide a common sense approach for the reduction of false alarm rates. For example, this technology uses a combination of microwave and PIR sensor circuitry within one housing
护送和访问控制
All visitors entering the facility should sign in and sign out on a visitor’s log to maintain accountability of who is in the facility, the timeframe of the visit, who they visited, and in the case of an emergency, have accountability of everyone for safety purposes.
the visitor is escorted at all times while inside the facility
Other types of visitor management systems use a computer-based system or specific visitor software product.
建筑物及其内部安全
Doors
Door assemblies include the door, its frame, and anchorage to the building.
Door Locks
锁具是普遍使用并具有较好的成本效益防护机制,能够遏制或延迟入侵行为,新型锁增加了出入记录功能,考虑了防钥匙丢失和复制的问题。
Electric Locks电子锁
Electric Strikes电控锁扣
Magnetic Locks磁力锁
Anti-Passback防跟踪检测设置
锁具类别
Rim Lock 弹簧锁
Mortise Lock暗锁
Locking Cylinders锁芯
Cipher Lock密码锁
密码锁使用键盘,并且可以编程
Hi-Tech Kevs
Intelligent keys”
“Instant keys
Safes保险柜
Tool-Resistant Safe Class TL-15.
hole through the door) for a net working time of 15 minutes using any combination of the following tools: a Mechanical or portable electric hand drills not exceeding one-half-inch size a Grinding points, carbide drills (excluding the magnetic drill press and other pressure-applying mechanisms, abrasive wheels, and rotating saws) a Common hand tools such as chisels, drifts, wrenches, screwdrivers, pliers, and hammers and sledges not to exceed the eight-pound size, pry bars and ripping tools not to exceed five feet in length a Picking tools that are not specially designed for use against a special make of safe.
要求
■ Weigh at least 750 pounds or be equipped with anchors and instructions for anchoring in larger safes, in concrete blocks, or to the floor of the bank premises. ■ Have metal in the body that is solid cast or fabricated open-hearth steel at least 1 inch thick with a tensile strength of 50,000 pounds per square inch (psi) and that is fastened to the floor in a manner equal to a continuous 1/4-inch - penetration weld of open-hearth steel having an ultimate tensile strength of 50,000psi. ■ Have the hole to permit insertion of electrical conductors for alarm devices not exceeding a 1/4-inch diameter and be provided in the top, side, bottom, or back of the safe body, but it must not permit a direct view of the door or locking mechanism. ■ Be equipped with a combination lock meeting UL Standard No. 768 requirements for Group 2, 1, or IR locks. ■ Be equipped with a relocking device that will effectively lock the door if the combination lock is punched
Vaults 储藏库
A vault (Figure 7.35) is defined as a room or compartment designed for the storage and safekeeping of valuables and has a size and shape that permits entrance and movement within by one or more persons.
■ Class M - One quarter hour
■ Class 1 - One half hour
■ Class 2 - One hour
■ Class 3 - Two hours
Containers
A container is a reinforced filling cabinet that can be used to store proprietary and sensitive information. 
Key Control
Key control, or more accurately the lack of key control, is one of the biggest risks that businesses and property owners face. Without a key control system, an organization cannot be sure who has keys or how many keys may have been produced for a given property
critical elements
2.1. Facility shall appoint a Key Control Authority or Key Control Manager to implement, execute, and enforce key control policies and procedures. 2.2. A policy and method for the issuing and collecting of all keys shall be implemented. 2.3. Keys and key blanks shall be stored in a locked cabinet or container, in a secured area. 2.4. A key control management program shall be utilized. A dedicated computer software application is preferred. 2.5. All keys shall remain the property of the issuing facility. 2.6. A key should be issued only to individuals who have a legitimate and official requirement for the key. 2.6.1. A requirement for access alone, when access can be accomplished by other means (such as unlocked doors, request for entry, intercoms, timers, etc.), shall not convey automatic entitlement to a key. 2.7. All keys shall be returned and accounted for. 2.8. Employees must ensure that keys are safeguarded and properly used. Personnel safety (e.g., duress, travel, monitoring)
人身安全
Personnel are often the greatest assets when designing physical and environmental security. Personnel are becoming more mobile and more concerned regarding their privacy be aware of privacy laws and expectations
Privacy 隐私
In most instances communication about the organization's privacy policies is key to ensuring privacy related complaints are minimized.
All individuals have an expectation of privacy
Travel 出行
YOU SHOULD KNOW
In most countries, you have no expectation of privacy in Internet cafes, hotels, offices, or public places. Hotel business centers and phone networks are regularly monitored in many countries. In some countries, hotel rooms are often searched. ■ All information you send electronically - by fax machine, personal digital assistant (PDA), computer, or telephone - can be intercepted. Wireless devices are especially vulnerable. ■ Security services and criminals can track your movements using your mobile phone or PDA and can turn on the microphone in your device even when you think it’s off. To prevent this, remove the battery. ■ Security services and criminals can also insert malicious software into your device through any connection they control. They can also do it wirelessly if your device is enabled for wireless. When you connect to your home server, the “malware” can migrate to your business, agency, or home system, can inventory your system, and can send information back to the security service or potential malicious actor. ■ Malware can also be transferred to your device through thumb drives (USB sticks), computer disks, and other “gifts.” ■ Transmitting sensitive government, personal, or proprietary information from abroad is therefore risky. ■ Corporate and government officials are most at risk, but do not assume you are too insignificant to be targeted. ■ Foreign security services and criminals are adept at “phishing” - that is, pretending to be someone you trust in order to obtain personal or sensitive information. ■ If a customs official demands to examine your device or if your hotel room is searched while the device is in the room and you are not, you should assume the device’s hard drive has been copied.
BEFORE YOU TRAVEL
■ If you can do without the device, don’t take it. ■ Do not take information you do not need, including sensitive contact information. Consider the consequences if your information were stolen by a foreign government or competitor. ■ Backup all information you take; leave the backed-up data at home. If feasible, use a different mobile phone or PDA from your usual one and remove the battery when not in use. In any case, have the device examined by your agency or company when you return. ■ Seek official cybersecurity alerts from: ■ www.onguardonline.gov and ■ ww'w.us-cert.gov/cas/tips
Prepare your device:
■ Create a strong password (numbers, upper and lowercase letters, special characters - at least 8 characters long). Never store passwords, phone numbers, or sign-on sequences on any device or in its case. ■ Change passwords at regular intervals (and as soon as you return). ■ Download current, up-to-date anti-virus protection, spyware protection, OS security patches, and a personal firewall. ■ Encrypt all sensitive information on the device. (But be warned: In some countries, customs officials may not permit you to enter with encrypted information.) ■ Update your Web browser with strict security settings. ■ Disable infrared ports and features you don’t need. ■ Use a virtual machine to run your desktop while travelling in order to ensure all changes made to the system are isolated within the virtual environment.
WHILE YOU'RE AWAY
■ Avoid transporting devices in checked baggage. ■ Use digital signature and encryption capabilities when possible. ■ Do not leave electronic devices unattended. If you have to stow them, remove the battery and SIM card and keep them with you. ■ Do not use thumb drives given to you; they may be compromised. Do not use your own thumb drive in a foreign computer for the same reason. If you’re required to do it anyway, assume you have been compromised; have your device cleaned as soon as you can. ■ Shield passwords from view. Do not use the “remember me” feature on many websites; retype the password every time. ■ Be aware of who is looking at your screen, especially in public areas. ■ Terminate connections when you’re not using them. ■ Clear your browser after each use: Delete history files, caches, cookies, URL, and temporary Internet files. ■ Do not open emails or attachments from unknown sources. Do not click on links in emails. Empty your “trash” and “recent” folders after every use. ■ Avoid Wi-Fi networks if you can. In some countries, they are controlled by security services; in all cases, they are insecure. ■ If your device or information is stolen, report it immediately to your home organization and the local U.S. embassy or consulate.
WHEN YOU RETURN
■ Change your password. Have your company or agency examine the device for the presence of malicious software. ■ For general travel alerts and information, see: ■ http://travel.state.gov/content/passports/english/alertswarnings.html
Duress 胁迫
Duress is a topic that relates to the concept of a person doing something or divulging something they normally would not under threat of harm. For example, an intruder may break into a data center and demand the receptionist cancel the alarm and tell the police it is a false alarm or the attacker will harm the receptionist. Scenario analysis can assist in determining the alternatives available and ensuring appropriate training and education can be conducted for individuals subject to duress