导图社区 Basic Cryptography 2
- 25
- 0
- 0
- 举报
Basic Cryptography 2
modern cryptography ,有Modern Symmetric Ciphers、Stream Ciphers、ChaCha20、BlockCipher...
编辑于2023-03-03 17:43:46- 2023年9月7日 Lecture1
Investment,其Future contracts:提前定好买卖价格,后面不管涨了还是跌了,盈亏自负,涨了,卖家亏钱,买家赚钱,跌了,买家亏钱,卖家赚钱
- Business Model
Business Model:Customer Segmentation、Value Proposition、Customer Relations、Revenue Streams……
- Basic Cryptography 2
modern cryptography ,有Modern Symmetric Ciphers、Stream Ciphers、ChaCha20、BlockCipher...
Basic Cryptography 2
社区模板帮助中心,点此进入>>
- 2023年9月7日 Lecture1
Investment,其Future contracts:提前定好买卖价格,后面不管涨了还是跌了,盈亏自负,涨了,卖家亏钱,买家赚钱,跌了,买家亏钱,卖家赚钱
- Business Model
Business Model:Customer Segmentation、Value Proposition、Customer Relations、Revenue Streams……
- Basic Cryptography 2
modern cryptography ,有Modern Symmetric Ciphers、Stream Ciphers、ChaCha20、BlockCipher...
- 相似推荐
- 大纲
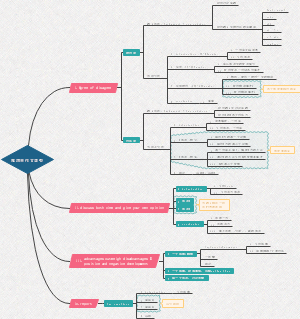
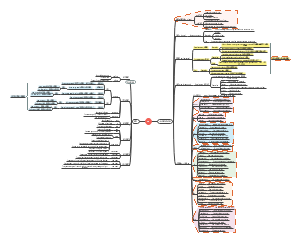
Basic Cryptography 2
Modern Symmetric Ciphers
deal with info in binary bit level
2 major approaches
Stream Ciphers
Block Ciphers
Stream Ciphers
key length 126bits,256 bits...
Maximum plaintext length: arbitrary long
synchronous V.S. asynchronous
security
secret key cannot be derived
the subsequenct segment of the keystream cannot be derived
ChaCha20
intro
by D.J. Berstein (2008)
refinement of Salsa20
Use a 256-bit key
8 * 32 bit
other input
4 * 32 bit constants
2 * 32 bit a nonce
2 * 32 bit a block counter
20 rounds
quarter round
(column0123 + diagonal 1234)* 10
design consideration
stream cipher eventually repeats
should have a large period
ChaCha20 2-word counter allow this
approximate the properties of a true random number stream as close as possible
ChaCha20, quarter-round functions allow high deffusion
Key should be long enough to resist brute-force atttack
ChaCha20 256-bits KEY
BlockCipher
brief
msg broke into fixed sized blocks
encrypted one block at a time
blocksize choice
small block size may be insecure
前后plaintext一样Ciphertext不一样
Block cipher principles
most symmetic block ciphers are based on Feistel Cipher Structure
Block cipher looks like a large substitution
create ciphertext from smaller building blocks
Claude Shannon & Substitution-Permutation Cipher
Shannon introduced the idea of substitution-permutation networks(1949)
form the basis of modern block ciphers
S-P network based on 2 prmitive cryptographics operations
substitution S-box
permutation P-box
provide confusion and diffusion of msg
completely obsecure statistical properties of original msg
Shannon suggest combining elements to obtain
Diffusion
子主题
confusion
every bit in cipher text should depend on as many bits as possible in the paintext and the key
Feistel Cipher
structure
Horst Feistel (IBM)
partition input blocks into two halves
implement Shannon's substitution-permutation network concept
design principle
Block size
improve block size, security ↑, decrypt speed↓
Key size
improve key size, security ↑, decrypt speed↓
number of rounds
improve round#,security ↑, decrypt speed↓
subkey gerneration
complexity ↑,security ↑, decrypt speed↓
round function
complexity ↑,security ↑, decrypt speed↓
fast software en/decryption & ease of analysis
recent concern for practical use
Data Encryption Standard (DES)
block cipher
both plaintext and cipher text 64 bits
KEY 64 bit (56-bit effective key)
input of DES
data broke into 64-bit blocks(add pad if necessary)
KEY (56-bit effective key + 8-bit parity bits)
DES Flow
64-bits plantext
initial permutation
broke into right half(32-bits) and left half(32-bits)
16 rounds of identical operations
data combined with 16 keys of 48-bits(derived from the 56-bit effective key)
L & R joined
final permutation
repeative
readily implementable in hardware and software
DES decryption
almost the same except that 16 sub-keys are entered in reverse order
subkey gerneration
odd parity
security of DES
recommanded minimum key size of any symmetric encryption schemes is 112-bits (80-bits for legacy system)
to give a better security margin, key size recommended to be at least 128-bits
Modes of Operations
Electronic codebook mode (ECB)
Cipher Block Chaining mode (CBC)
Cipher feedback mode (CFB)
Output feedback mode (OFB)
Counter mode (CTR)